- DOI: 10.6084/M9.FIGSHARE.1145884
- Corpus ID: 6612474

Cloud Computing: Overview & Current Research Challenges
- Published 2012
- Computer Science, Engineering
- IOSR Journal of Computer Engineering
Figures from this paper

80 Citations
Security threats with associated mitigation techniques in cloud computing.
- Highly Influenced
A Comprehensive Review on Cloud Computing and Cloud Security Issues
Profit maximization scheme with guaranteed quality of service in cloud computing, what is cloud computing, cloud computing – a market perspective and research directions, load balancing techniques in cloud computing environment: a review, storage architecture for network security in cloud computing, issues and challenges in management related to information technology, a review on cloud computing and its security issues, effect of cloud computing system in education, 48 references, cloud computing: security issues and research challenges, cloud computing future framework for e-management of ngo's.
- Highly Influential
A Survey on Security Issues in Cloud Computing
Cloud computing is changing how we communicate, a survey on security issues in service delivery models of cloud computing, on technical security issues in cloud computing, cloud computing, implementation of cloud computing on web application, a taxonomy and survey of cloud computing systems, cloud security issues, related papers.
Showing 1 through 3 of 0 Related Papers
Systematic Literature Review of Cloud Computing Research Between 2010 and 2023
- Conference paper
- First Online: 21 May 2024
- Cite this conference paper

- Shailaja Jha 10 &
- Devina Chaturvedi ORCID: orcid.org/0009-0004-1242-2099 11
Part of the book series: Lecture Notes in Business Information Processing ((LNBIP,volume 508))
Included in the following conference series:
- Workshop on e-Business
137 Accesses
We present a meta-analysis of cloud computing research in information systems. The study includes 152 referenced journal articles published between January 2010 to June 2023. We take stock of the literature and the associated research themes, research frameworks, the employed research methodology, and the geographical distribution of the articles. This review provides holistic insights into trends in cloud computing research based on themes, frameworks, methodology, geographical focus, and future research directions. The results indicate that the extant literature tends to skew toward themes related to business issues, which is an indicator of the maturing and widespread use of cloud computing. This trend is evidenced in the more recent articles published between 2016 to 2023.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
Subscribe and save.
- Get 10 units per month
- Download Article/Chapter or eBook
- 1 Unit = 1 Article or 1 Chapter
- Cancel anytime
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
The conference proceedings were primarily used to assess the year-on-year numerical trends in publications, and they have not been used for detailed analysis.
Abdalla Mikhaeil, C., James, T.L.: Examining the case of French hesitancy toward IDaaS solutions: technical and social contextual factors of the organizational IDaaS privacy calculus. Inform. Manage. 60 (4), 103779 (2023)
Google Scholar
Allen, B., et al.: Software as a service for data scientists. Commun. ACM 55 (2), 81–88 (2012)
Andrade-Rojas, M.G., Kathuria, A., Lee, H.-H.: Multilevel synergy of IT operational integration: competition networks and operating performance. Prod. Oper. Manage. (forthcoming) (2024)
Andrade-Rojas, M.G., Saldanha, T., Kathuria, A., Khuntia, J., Boh, W.F.: How IT overcomes deficiencies for innovation in SMEs: closed innovation versus open innovation. Inform. Syst. Res. (forthcoming) (2024)
Anthes, G.: Security in the cloud. Commun. ACM 53 , 16–18 (2010)
Armbrust, M., et al.: A view of cloud computing. Commun. ACM 53 , 50–58 (2010)
August, T., Niculescu, M.F., Shin, H.: Cloud implications on software network structure and security risks. Inform. Syst. Res. 25 , 489–510 (2014)
Bandara, W., Furtmueller, E., Gorbacheva, E., Miskon, S., Beekhuyzen, J.: Achieving rigor in literature reviews: insights from qualitative data analysis and tool-support. Commun. Assoc. Inform. Syst. 37 (8), 154–204 (2015). http://aisel.aisnet.org/cais/vol37/iss1/8
Benlian, A.: Is traditional, open-source, or on-demand first choice? Developing an AHP-based framework for the comparison of different software models in office suites selection. Eur. J. Inform. Syst. 20 , 542–559 (2011)
Benlian, A., Kettinger, W.J., Sunyaev, A., Winkler, T.J.: Special section: the transformative value of cloud computing: a decoupling, platformization, and recombination theoretical framework. J. Manage. Inform. Syst. 35 , 719–739 (2018)
Benlian, A., Koufaris, M., Hess, T.: The role of SaaS service quality for continued SaaS use: Empirical insights from SaaS using firms (2010)
Bhattacherjee, A., Park, S.C.: Why end-users move to the cloud: a migration-theoretic analysis. Eur. J. Inform. Syst. 23, 357–372 (2014)
Chaturvedi, D., Kathuria, A., Andrade, M., Saldanha, T.: Navigating the Paradox of IT Novelty and Strategic Conformity: The Moderating Role of Industry Dynamism (2023)
Chen, F., Lu, A., Wu, H., Li, M.: Compensation and pricing strategies in cloud service SLAs: considering participants’ risk attitudes and consumer quality perception. Electron. Commerce Res. Appl. 56 , 101215 (2022)
Cheng, H.K., Li, Z., Naranjo, A.: Research note—cloud computing spot pricing dynamics: latency and limits to arbitrage. Inform. Syst. Res. 27 , 145–165 (2016)
Choudhary, V., Vithayathil, J.: The impact of cloud computing: should the IT department be organized as a cost center or a profit center? J. Manage. Inform. Syst. 30 , 67–100 (2013)
Choudhary, V., Zhang, Z.: Research note—patching the cloud: the impact of SaaS on patching strategy and the timing of software release. Inform. Syst. Res. 26 , 845–858 (2015)
Dasgupta, A., Karhade, P., Kathuria, A., Konsynski, B.: Holding space for voices that do not speak: design reform of rating systems for platforms in GREAT economies (2021)
Demirkan, H., Cheng, H.K., Bandyopadhyay, S.: Coordination strategies in an SaaS supply chain. J. Manage. Inform. Syst. 26 , 119–143 (2010)
Demirkan, H., Delen, D.: Leveraging the capabilities of service-oriented decision support systems: putting analytics and big data in cloud. Decis. Support Syst. 55 , 412–421 (2013)
Dierks, L., Seuken, S.: Cloud pricing: the spot market strikes back. Manage. Sci. 68 (1), 105–122 (2022)
Article Google Scholar
Ding, S., Xia, C., Wang, C., Desheng, Wu., Zhang, Y.: Multi-objective optimization based ranking prediction for cloud service recommendation. Decis. Support. Syst. 101 , 106–114 (2017)
Dong, L., Shu, W., Sun, D., Li, X., Zhang, L.: Pre-alarm system based on real-time monitoring and numerical simulation using internet of things and cloud computing for tailings dam in mines. IEEE Access 5 , 21080–21089 (2017)
Xin, Du., Tang, S., Zhihui, Lu., Gai, K., Jie, Wu., Hung, P.C.K.: Scientific workflows in IoT environments: a data placement strategy based on heterogeneous edge-cloud computing. ACM Trans. Manage. Inform. Syst. 13 (4), 1–26 (2022)
Ermakova, T., Fabian, B., Kornacka, M., Thiebes, S., Sunyaev, A.: Security and privacy requirements for cloud computing in healthcare: elicitation and prioritization from a patient perspective. ACM Trans. Manage. Inform. Syst. 11 (2), 1–29 (2020)
Garrison, G., Kim, S., Wakefield, R.L.: Success factors for deploying cloud computing. Commun. ACM 55 (9), 62–68 (2012)
Giessmann, A., Legner, C.: Designing business models for cloud platforms. Inf. Syst. J. 26 (5), 551–579 (2016). https://doi.org/10.1111/isj.12107
Gray, A.: Conflict of laws and the cloud. Comput. Law Secur. Rev. 29 (1), 58–65 (2013)
Hosseini, L., Tang, S., Mookerjee, V., Sriskandarajah, C.: A switch in time saves the dime: a model to reduce rental cost in cloud computing. Inform. Syst. Res. 31 (3), 753–775 (2020)
Huang, K.-W., Sundararajan, A.: Pricing digital goods: discontinuous costs and shared infrastructure. Inf. Syst. Res. 22 (4), 721–738 (2011)
Iosup, A., Ostermann, S., Yigitbasi, M.N., Prodan, R., Fahringer, T., Epema, D.H.J.: Performance analysis of cloud computing services for many-tasks scientific computing. IEEE Trans. Parallel Distrib. Syst. 22 , 931–945 (2011)
Iyer, B., Henderson, J.C.: Preparing for the future: understanding the seven capabilities cloud computing. MIS Q. Exec. 9 , 2 (2010)
Jha, S. and Kathuria, A. Size Matters for Cloud Capability and Performance (2022)
Jha, S., Kathuria, A.: How firm age and size influence value creation from cloud computing (2023)
Joe-Wong, C., Sen, S.: Harnessing the power of the cloud: revenue, fairness, and cloud neutrality. J. Manage. Inf. Syst. 35 , 813–836 (2018)
Joint, A., Baker, E.: Knowing the past to understand the present–issues in the contracting for cloud based services. Comput. Law Secur. Rev. 27 (4), 407–415 (2011)
Karhade, P., Kathuria, A.: Missing impact of ratings on platform participation in India: a call for research in GREAT domains. Commun. Assoc. Inf. Syst. 47 (1), 19 (2020)
Karhade, P., Kathuria, A., Dasgupta, A., Malik, O., Konsynski, B.R.: Decolonization of digital platforms: a research agenda for GREAT domains. In: Garimella, A., Karhade, P., Kathuria, A., Liu, X., Xu, J., Zhao, K. (eds.) The Role of e-Business during the Time of Grand Challenges. LNBIP, vol. 418, pp. 51–58. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-79454-5_5
Chapter Google Scholar
Karhade, P., Kathuria, A., Konsynski, B.: When choice matters: assortment and participation for performance on digital platforms (2021)
Kathuria, A., Karhade, P.P., Konsynski, B.R.: In the realm of hungry ghosts: multi-level theory for supplier participation on digital platforms. J. Manag. Inf. Syst. 37 (2), 396–430 (2020)
Kathuria, A., Mann, A., Khuntia, J., Saldanha, T.J.V., Kauffman, R.J.: A strategic value appropriation path for cloud computing. J. Manage. Inf. Syst. 35 (3), 740–775 (2018). https://doi.org/10.1080/07421222.2018.1481635
Kaur, J., Kaur, P.D.: CE-GMS: A cloud IoT-enabled grocery management system. Electron. Commer. Res. Appl. 28 , 63–72 (2018)
Kepes, B.: 30% of servers are sitting “Comatose” according to research. Forbes https://forbes.com/sites/benkepes/2015/06/03/30-of-servers-are-sitting-comatose-according-to-research (2015)
Khokhar, R.H., Fung, B.C.M., Iqbal, F., Alhadidi, D., Bentahar, J.: Privacy-preserving data mashup model for trading person-specific information. Electron. Commer. Res. Appl. 17 , 19–37 (2016)
Khuntia, J., Kathuria, A., Andrade-Rojas, M.G., Saldanha, T., Celly, N.: How foreign and domestic firms differ in leveraging IT-enabled supply chain information integration in BOP markets: the role of supplier and client business collaboration. J. Assoc. Inf. Syst. 22 (3), 6 (2021)
King, W.R., He, J.: Understanding the role and methods of meta-analysis in IS Research. Commun. Assoc. Inf. Syst. 16, 665–686 (2005)
Krancher, O., Luther, P., Jost, M.: Key affordances of Platform-as-a-Service: self-organization and continuous feedback. J. Manage. Inf. Syst. 35 , 776–812 (2018)
Kumar, C., Marston, S., Sen, R., Narisetty, A.: Greening the cloud: a load balancing mechanism to optimize cloud computing networks. J. Manage. Inf. Syst. 39 ,, 513–541 (2022)
Kung, L., Cegielski, C.G., Kung, H.-J.: An integrated environmental perspective on software as a service adoption in manufacturing and retail firms. J. Inf. Technol. 30 , 352–363 (2015)
Lansing, J., Benlian, A., Sunyaev, A.: Unblackboxing” decision makers’ interpretations of IS certifications in the context of cloud service certifications. J. Assoc. Inf. Syst. 19 (11), 1064–1096 (2018)
Lansing, J., Siegfried, N., Sunyaev, A., Benlian, A.: Strategic signaling through cloud service certifications: Comparing the relative importance of certifications’ assurances to companies and consumers. J. Strateg. Inf. Syst. 28 , 101579 (2019)
Lansing, J., Sunyaev, A.: Trust in cloud computing. ACM SIGMIS Database DATABASE Adv. Inform. Syst. 47 , 58–96 (2016)
Lee, J., Cho, D., Lim, G.: Design and validation of the bright internet. J. Assoc. Inform. Syst. 19 , 63–85 (2018)
Lee, M.H., Han, S.P., Park, S., Oh, W.: Positive demand spillover of popular app adoption: implications for platform owners’ management of complements. Inf. Syst. Res. 34 (3), 961–995 (2023)
Li, S., Chen, W., Chen, Y., Chen, C. and Zheng, Z.: Makespan-minimized computation offloading for smart toys in edge-cloud computing. Electron. Commerce Res. Appl. 37 , 100884 (2019)
Li, S., Cheng, H.K., Duan, Y., Yang, Y.-C.: A study of enterprise software licensing models. J. Manag. Inf. Syst. 34 (1), 177–205 (2017)
Lins, S., Schneider, S., Szefer, J., Ibraheem, S., Ali, A.: Designing monitoring systems for continuous certification of cloud services: deriving meta-requirements and design guidelines. Commun. Assoc. Inf. Syst. 44 (1), 460–510 (2019)
Liu, Y., Sheng, X., Marston, S.R.: The impact of client-side security restrictions on the competition of cloud computing services. Int. J. Electron. Comm. 19 (3), 90–117 (2015)
Ma, D., Seidmann, A.: Analyzing software as a service with per-transaction charges. Inf. Syst. Res. 26 , 360–378 (2015)
Malik, O., Jaiswal, A., Kathuria, A., Karhade, P.: Leveraging BI systems to overcome infobesity: a comparative analysis of incumbent and new entrant firms (2022)
Mani, D., Srikanth, K., Bharadwaj, A.: Efficacy of R&D work in offshore captive centers: an empirical study of task characteristics, coordination mechanisms, and performance. Inf. Syst. Res. 25 (4), 846–864 (2014)
Mann, A., Kathuria, A., Khuntia, J., Saldanha, T.: Cloud-integration and business flexibility: the mediating role of cloud functional capabilities (2016)
Marston, S., Li, Z., Bandyopadhyay, S., Zhang, J., Ghalsasi, A.: Cloud computing — the business perspective. Decis. Support. Syst. 51 (1), 176–189 (2011)
Mell, P.M., Grance, T.: The NIST definition of cloud computing. National Institute of Standards and Technology (2011)
Metz, C.: The epic story of dropboxs exodus from the amazon cloud empire (2016)
Mithas, R., Sambamurthy,: How information management capability influences firm performance. MIS Q. 35 (1), 237 (2011)
Mithas, T., Bardhan, G.: Information technology and firm profitability: mechanisms and empirical evidence. MIS Q. 36 (1), 205 (2012)
Muhic, M., Bengtsson, L., Holmström, J.: Barriers to continuance use of cloud computing: evidence from two case studies. Inf. Manage. 60 , 103792 (2023)
Mukherjee, A., Sundarraj, R.P., Dutta, K.: Time-preference-based on-spot bundled cloud-service provisioning. Decis. Support. Syst. 151 , 113607 (2021)
Müller, S.D., Holm, S.R., Søndergaard, J.: Benefits of cloud computing: literature review in a maturity model perspective. Commun. Assoc. Inform. Syst. 37 , 851–878 (2015)
Ojala, A.: Business models and opportunity creation: how IT entrepreneurs create and develop business models under uncertainty. Inf. Syst. J. 26 , 451–476 (2015)
Oliveira, T., Thomas, M., Espadanal, M.: Assessing the determinants of cloud computing adoption: An analysis of the manufacturing and services sectors. Inf. Manage. 51 , 497–510 (2014)
Owens, D. Securing elasticity in the cloud. Communications of the ACM , 53, 6 (2010/06 2010), 46–51 (2010)
Pang, M.-S., Tanriverdi, H.: Strategic roles of IT modernization and cloud migration in reducing cybersecurity risks of organizations: the case of U.S. federal government. J. Strat. Inf. Syst. 31 , 101707 (2022)
Park, J., Han, K., Lee, B.: Green cloud? An empirical analysis of cloud computing and energy efficiency. Manage. Sci. 69 , 1639–1664 (2023)
Parno, B., Howell, J., Gentry, C., Raykova, M.: Pinocchio. Commun. ACM 59 , 103–112 (2016)
Pye, J., Rai, A., Dong, J.Q.: Business value of information technology capabilities: an institutional governance perspective. Inf. Syst. Res. 35 , 28–44 (2023)
Ramakrishnan, T., Kathuria, A., Khuntia, J., Konsynski, B.: IoT value creation through supply chain analytics capability (2022)
Retana, G., Forman, C., Narasimhan, S., Niculescu, M.F., Wu, D.J.: Technical support, knowledge transfer, and service demand: evidence from the cloud. SSRN Electron. J. (2012)
Rodrigues, J., Ruivo, P., Oliveira, T.: Mediation role of business value and strategy in firm performance of organizations using software-as-a-service enterprise applications. Inf. Manag. 58 (1), 103289 (2021)
Saldanha, T.J., Andrade-Rojas, M.G., Kathuria, A., Khuntia, J., Krishnan, M.: How the locus of uncertainty shapes the influence of CEO long-term compensation on IT capital investments. MIS Q. (2023)
Sambhara, C., Rai, A., Xu, S.X.: Configuring the enterprise systems portfolio: the role of information risk. Inf. Syst. Res. 33 (2), 446–463 (2022)
Sarker, S., Chatterjee, S., Xiao, X., Elbanna, A.: The sociotechnical axis of cohesion for the IS discipline: its historical legacy and its continued relevance. MIS Q. 43 (3), 695–720 (2019)
Schlagwein, D., Thorogood, A., Willcocks, L.P.: How commonwealth bank of Australia gained benefits using a standards-based, multi-provider cloud model. MIS Q. Exec. 13 (4), 209–222 (2014)
Schneider, S., Sunyaev, A.: Determinant factors of cloud-sourcing decisions: reflecting on the IT outsourcing literature in the era of cloud computing. J. Inf. Technol. 31 (1), 1–31 (2016). https://doi.org/10.1057/jit.2014.25
Schneider, S., Wollersheim, J., Krcmar, H., Sunyaev, A.: How do Requirements evolve over Time? A case study investigating the role of context and experiences in the evolution of enterprise software requirements. J. Inf. Technol. 33 (2), 151–170 (2018)
Schniederjans, D.G., Hales, D.N.: Cloud computing and its impact on economic and environmental performance: a transaction cost economics perspective. Decis. Support. Syst. 86 , 73–82 (2016)
Schreieck, M., Wiesche, M., Krcmar, H.: Capabilities for value co-creation and value capture in emergent platform ecosystems: a longitudinal case study of SAP’s cloud platform. J. Inf. Technol. 36 (4), 365–390 (2021)
Shiau, W.-L., Chau, P.Y.K.: Understanding behavioral intention to use a cloud computing classroom: a multiple model comparison approach. Inf. Manag. 53 (3), 355–365 (2016)
Singh, V.K., Shivendu, S., Dutta, K.: Spot instance similarity and substitution effect in cloud spot market. Decis. Support. Syst. 159 , 113815 (2022)
Soh, F., Setia, P.: The impact of dominant IT infrastructure in multi-establishment firms: the moderating role of environmental dynamism. J. Assoc. Inf. Syst. 23 (6), 1603–1633 (2022)
Son, I., Lee, D., Lee, J.-N., Chang, Y.B.: Market perception on cloud computing initiatives in organizations: an extended resource-based view. Inf. Manag. 51 (6), 653–669 (2014)
Srinivasan, S.: Is security realistic in cloud computing? J. Int. Technol. Inf. Manag. 22 (4), 3 (2013). https://doi.org/10.58729/1941-6679.1020
Article MathSciNet Google Scholar
Sun, T., Shi, L., Viswanathan, S., Zheleva, E.: Motivating effective mobile app adoptions: evidence from a large-scale randomized field experiment. Inf. Syst. Res. 30 (2), 523–539 (2019)
Templier, M., Paré, G.: Transparency in literature reviews: an assessment of reporting practices across review types and genres in top IS journals. Eur. J. Inf. Syst. 27 (5), 503–550 (2017). https://doi.org/10.1080/0960085X.2017.1398880
Trenz, M., Huntgeburth, J., Veit, D.: Uncertainty in cloud service relationships: uncovering the differential effect of three social influence processes on potential and current users. Inf. Manage. 55, 971–983 (2018)
van de Weerd, I., Mangula, I.S., Brinkkemper, S.: Adoption of software as a service in Indonesia: examining the influence of organizational factors. Inf. Manage. 53 (7), 915–928 (2016)
Venkatesh, V., Bala, H., Sambamurthy, V.: Implementation of an information and communication technology in a developing country: a multimethod longitudinal study in a Bank in India. Inf. Syst. Res. 27 (3), 558–579 (2016)
Venkatesh, V., Sykes, T.A.: Digital divide initiative success in developing countries: a longitudinal field study in a Village in India. Inf. Syst. Res. 24 (2), 239–260 (2013)
Venters, W., Whitley, E.A.: A critical review of cloud computing: researching desires and realities. J. Inf. Technol. 27 (3), 179–197 (2012)
Wang, N., Huigang Liang, Yu., Jia, S.G., Xue, Y., Wang, Z.: Cloud computing research in the IS discipline: a citation/co-citation analysis. Decis. Support. Syst. 86 , 35–47 (2016)
Wang, X., Wang, X.: Multimedia data delivery based on IoT clouds. Commun. ACM 64 (8), 80–86 (2021)
Winkler, T.J., Benlian, A., Piper, M., Hirsch, H.: Bayer healthcare delivers a dose of reality for cloud payoff mantras in multinationals. MIS Q. Exec. 13 , 4 (2014)
Winkler, T.J., Brown, C.V.: Horizontal allocation of decision rights for on-premise applications and Software-as-a-Service. J. Manage. Inf. Syst. 30 (3), 13–48 (2013)
Wright, R.T., Roberts, N., Wilson, D.: The role of context in IT assimilation: a multi-method study of a SaaS platform in the US nonprofit sector. Eur. J. Inf. Syst. 26 (5), 509–539 (2017). https://doi.org/10.1057/s41303-017-0053-2
Wulf, F., Lindner, T., Strahringer, S., Westner, M.: IaaS, PaaS, or SaaS? The why of cloud computing delivery model selection: vignettes on the post-adoption of cloud computing. In: The Proceedings of Proceedings of the 54th Hawaii International Conference on System Sciences, pp. 6285–6294 (2021)
Xiong, Hu., Wang, Yi., Li, W., Chen, C.-M.: Flexible, efficient, and secure access delegation in cloud computing. ACM Trans. Manage. Inf. Syst. 10 (1), 1–20 (2019)
Yang, H., Tate, M.: A descriptive literature review and classification of cloud computing research. Commun. Assoc. Inf. Syst. 31 (1), 2 (2012)
Yaraghi, N., Du, A.Y., Sharman, R., Gopal, R.D., Ramesh, R.: Health Information exchange as a multisided platform: adoption, usage, and practice involvement in service co-production. Inf. Syst. Res. 26 (1), 1–18 (2015)
Yuan, S., Sanjukta Das, R., Ramesh, C.Q.: Service agreement trifecta: backup resources, price and penalty in the availability-aware cloud. Inf. Syst. Res. 29 (4), 947–964 (2018)
Zhang, G., Ravishankar, M.N.: Exploring vendor capabilities in the cloud environment: a case study of Alibaba cloud computing. Inf. Manage. 56 , 343–355 (2019)
Zhang, X., Yue, W.: Integration of on-premises and cloud-based software: the product bundling perspective. J. Assoc. Inform. Syst. 21 , 1507–1551 (2020)
Zorrilla, M., García-Saiz, D.: A service oriented architecture to provide data mining services for non-expert data miners. Decis. Support. Syst.. Support. Syst. 55 (1), 399–411 (2013). https://doi.org/10.1016/j.dss.2012.05.045
Download references
Author information
Authors and affiliations.
SP Jain Institute of Management and Research, Mumbai, India
Shailaja Jha
Indian School of Business, Hyderabad, India
Devina Chaturvedi
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Devina Chaturvedi .
Editor information
Editors and affiliations.
#6104, Indian School of Business, Hyderabad, Telangana, India
Abhishek Kathuria
Chinese University of Hong Kong, Sha Tin District, Hong Kong
Prasanna P. Karhade
University of North Carolina at Charlotte, Charlotte, NC, USA
Indian School of Business, Hyderabad, Telangana, India
Rights and permissions
Reprints and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper.
Jha, S., Chaturvedi, D. (2024). Systematic Literature Review of Cloud Computing Research Between 2010 and 2023. In: Kathuria, A., Karhade, P.P., Zhao, K., Chaturvedi, D. (eds) Digital Transformation in the Viral Age. WeB 2022. Lecture Notes in Business Information Processing, vol 508. Springer, Cham. https://doi.org/10.1007/978-3-031-60003-6_5
Download citation
DOI : https://doi.org/10.1007/978-3-031-60003-6_5
Published : 21 May 2024
Publisher Name : Springer, Cham
Print ISBN : 978-3-031-60002-9
Online ISBN : 978-3-031-60003-6
eBook Packages : Computer Science Computer Science (R0)
Share this paper
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
- Original Papers
- Open access
- Published: 20 April 2010
Cloud computing: state-of-the-art and research challenges
- Qi Zhang 1 ,
- Lu Cheng 1 &
- Raouf Boutaba 1
Journal of Internet Services and Applications volume 1 , pages 7–18 ( 2010 ) Cite this article
93k Accesses
2077 Citations
28 Altmetric
Metrics details
Cloud computing has recently emerged as a new paradigm for hosting and delivering services over the Internet. Cloud computing is attractive to business owners as it eliminates the requirement for users to plan ahead for provisioning, and allows enterprises to start from the small and increase resources only when there is a rise in service demand. However, despite the fact that cloud computing offers huge opportunities to the IT industry, the development of cloud computing technology is currently at its infancy, with many issues still to be addressed. In this paper, we present a survey of cloud computing, highlighting its key concepts, architectural principles, state-of-the-art implementation as well as research challenges. The aim of this paper is to provide a better understanding of the design challenges of cloud computing and identify important research directions in this increasingly important area.
Al-Fares M et al (2008) A scalable, commodity data center network architecture. In: Proc SIGCOMM
Amazon Elastic Computing Cloud, aws.amazon.com/ec2
Amazon Web Services, aws.amazon.com
Ananthanarayanan R, Gupta K et al (2009) Cloud analytics: do we really need to reinvent the storage stack? In: Proc of HotCloud
Armbrust M et al (2009) Above the clouds: a Berkeley view of cloud computing. UC Berkeley Technical Report
Berners-Lee T, Fielding R, Masinter L (2005) RFC 3986: uniform resource identifier (URI): generic syntax, January 2005
Bodik P et al (2009) Statistical machine learning makes automatic control practical for Internet datacenters. In: Proc HotCloud
Brooks D et al (2000) Power-aware microarchitecture: design and modeling challenges for the next-generation microprocessors, IEEE Micro
Chandra A et al (2009) Nebulas: using distributed voluntary resources to build clouds. In: Proc of HotCloud
Chang F, Dean J et al (2006) Bigtable: a distributed storage system for structured data. In: Proc of OSDI
Chekuri C, Khanna S (2004) On multi-dimensional packing problems. SIAM J Comput 33(4):837–851
Article MATH MathSciNet Google Scholar
Church K et al (2008) On delivering embarrassingly distributed cloud services. In: Proc of HotNets
Clark C, Fraser K, Hand S, Hansen JG, Jul E, Limpach C, Pratt I, Warfield A (2005) Live migration of virtual machines. In: Proc of NSDI
Cloud Computing on Wikipedia, en.wikipedia.org/wiki/Cloudcomputing , 20 Dec 2009
Cloud Hosting, CLoud Computing and Hybrid Infrastructure from GoGrid, http://www.gogrid.com
Dean J, Ghemawat S (2004) MapReduce: simplified data processing on large clusters. In: Proc of OSDI
Dedicated Server, Managed Hosting, Web Hosting by Rackspace Hosting, http://www.rackspace.com
FlexiScale Cloud Comp and Hosting, www.flexiscale.com
Ghemawat S, Gobioff H, Leung S-T (2003) The Google file system. In: Proc of SOSP, October 2003
Google App Engine, URL http://code.google.com/appengine
Greenberg A, Jain N et al (2009) VL2: a scalable and flexible data center network. In: Proc SIGCOMM
Guo C et al (2008) DCell: a scalable and fault-tolerant network structure for data centers. In: Proc SIGCOMM
Guo C, Lu G, Li D et al (2009) BCube: a high performance, server-centric network architecture for modular data centers. In: Proc SIGCOMM
Hadoop Distributed File System, hadoop.apache.org/hdfs
Hadoop MapReduce, hadoop.apache.org/mapreduce
Hamilton J (2009) Cooperative expendable micro-slice servers (CEMS): low cost, low power servers for Internet-scale services In: Proc of CIDR
IEEE P802.3az Energy Efficient Ethernet Task Force, www.ieee802.org/3/az
Kalyvianaki E et al (2009) Self-adaptive and self-configured CPU resource provisioning for virtualized servers using Kalman filters. In: Proc of international conference on autonomic computing
Kambatla K et al (2009) Towards optimizing Hadoop provisioning in the cloud. In: Proc of HotCloud
Kernal Based Virtual Machine, www.linux-kvm.org/page/MainPage
Krautheim FJ (2009) Private virtual infrastructure for cloud computing. In: Proc of HotCloud
Kumar S et al (2009) vManage: loosely coupled platform and virtualization management in data centers. In: Proc of international conference on cloud computing
Li B et al (2009) EnaCloud: an energy-saving application live placement approach for cloud computing environments. In: Proc of international conf on cloud computing
Meng X et al (2010) Improving the scalability of data center networks with traffic-aware virtual machine placement. In: Proc INFOCOM
Mysore R et al (2009) PortLand: a scalable fault-tolerant layer 2 data center network fabric. In: Proc SIGCOMM
NIST Definition of Cloud Computing v15, csrc.nist.gov/groups/SNS/cloud-computing/cloud-def-v15.doc
Osman S, Subhraveti D et al (2002) The design and implementation of zap: a system for migrating computing environments. In: Proc of OSDI
Padala P, Hou K-Y et al (2009) Automated control of multiple virtualized resources. In: Proc of EuroSys
Parkhill D (1966) The challenge of the computer utility. Addison-Wesley, Reading
Google Scholar
Patil S et al (2009) In search of an API for scalable file systems: under the table or above it? HotCloud
Salesforce CRM, http://www.salesforce.com/platform
Sandholm T, Lai K (2009) MapReduce optimization using regulated dynamic prioritization. In: Proc of SIGMETRICS/Performance
Santos N, Gummadi K, Rodrigues R (2009) Towards trusted cloud computing. In: Proc of HotCloud
SAP Business ByDesign, www.sap.com/sme/solutions/businessmanagement/businessbydesign/index.epx
Sonnek J et al (2009) Virtual putty: reshaping the physical footprint of virtual machines. In: Proc of HotCloud
Srikantaiah S et al (2008) Energy aware consolidation for cloud computing. In: Proc of HotPower
Urgaonkar B et al (2005) Dynamic provisioning of multi-tier Internet applications. In: Proc of ICAC
Valancius V, Laoutaris N et al (2009) Greening the Internet with nano data centers. In: Proc of CoNext
Vaquero L, Rodero-Merino L, Caceres J, Lindner M (2009) A break in the clouds: towards a cloud definition. ACM SIGCOMM computer communications review
Vasic N et al (2009) Making cluster applications energy-aware. In: Proc of automated ctrl for datacenters and clouds
Virtualization Resource Chargeback, www.vkernel.com/products/EnterpriseChargebackVirtualAppliance
VMWare ESX Server, www.vmware.com/products/esx
Windows Azure, www.microsoft.com/azure
Wood T et al (2007) Black-box and gray-box strategies for virtual machine migration. In: Proc of NSDI
XenSource Inc, Xen, www.xensource.com
Zaharia M et al (2009) Improving MapReduce performance in heterogeneous environments. In: Proc of HotCloud
Zhang Q et al (2007) A regression-based analytic model for dynamic resource provisioning of multi-tier applications. In: Proc ICAC
Download references
Author information
Authors and affiliations.
University of Waterloo, Waterloo, Ontario, Canada, N2L 3G1
Qi Zhang, Lu Cheng & Raouf Boutaba
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Raouf Boutaba .
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License ( https://creativecommons.org/licenses/by/2.0 ), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Reprints and permissions
About this article
Cite this article.
Zhang, Q., Cheng, L. & Boutaba, R. Cloud computing: state-of-the-art and research challenges. J Internet Serv Appl 1 , 7–18 (2010). https://doi.org/10.1007/s13174-010-0007-6
Download citation
Received : 08 January 2010
Accepted : 25 February 2010
Published : 20 April 2010
Issue Date : May 2010
DOI : https://doi.org/10.1007/s13174-010-0007-6
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cloud computing
- Data centers
- Virtualization
Advances, Systems and Applications
- Open access
- Published: 06 August 2022
Big data analytics in Cloud computing: an overview
- Blend Berisha 1 ,
- Endrit Mëziu 1 &
- Isak Shabani 1
Journal of Cloud Computing volume 11 , Article number: 24 ( 2022 ) Cite this article
38k Accesses
43 Citations
10 Altmetric
Metrics details
Big Data and Cloud Computing as two mainstream technologies, are at the center of concern in the IT field. Every day a huge amount of data is produced from different sources. This data is so big in size that traditional processing tools are unable to deal with them. Besides being big, this data moves fast and has a lot of variety. Big Data is a concept that deals with storing, processing and analyzing large amounts of data. Cloud computing on the other hand is about offering the infrastructure to enable such processes in a cost-effective and efficient manner. Many sectors, including among others businesses (small or large), healthcare, education, etc. are trying to leverage the power of Big Data. In healthcare, for example, Big Data is being used to reduce costs of treatment, predict outbreaks of pandemics, prevent diseases etc. This paper, presents an overview of Big Data Analytics as a crucial process in many fields and sectors. We start by a brief introduction to the concept of Big Data, the amount of data that is generated on a daily bases, features and characteristics of Big Data. We then delve into Big Data Analytics were we discuss issues such as analytics cycle, analytics benefits and the movement from ETL to ELT paradigm as a result of Big Data analytics in Cloud. As a case study we analyze Google’s BigQuery which is a fully-managed, serverless data warehouse that enables scalable analysis over petabytes of data. As a Platform as a Service (PaaS) supports querying using ANSI SQL. We use the tool to perform different experiments such as average read, average compute, average write, on different sizes of datasets.
Introduction
We live in the data age. We see them everywhere and this is due to the great technological developments that have taken place in recent years. The rate of digitalization has increased significantly and now we are rightly talking about” digital information societies”. If 20 or 30 years ago only 1% of the information produced was digital, now over 94% of this information is digital and it comes from various sources such as our mobile phones, servers, sensor devices on the Internet of Things, social networks, etc. [ 1 ]. The year 2002 is considered the” beginning of the digital age” where an explosion of digitally produced equipment and information was seen.
The number and amount of information collected has increased significantly due to the increase of devices that collect this information such as mobile devices, cheap and numerous sensor devices on the Internet of Things (IoT), remote sensing, software logs, cameras, microphones, RFID readers, wireless sensor networks, etc. [ 2 ]. According to statistics, the amount of data generated / day is about 44 zettabytes (44 × 10 21 bytes). Every second, 1.7 MB of data is generated per person [ 3 ]. Based on International Data Group forecasts, the global amount of data will increase exponentially from 2020 to 2025, with a move from 44 to 163 zettabytes [ 4 ]. Figure 1 shows the amount of global data generated, copied and consumed. As can be seen, in the years 2010–2015, the rate of increase from year to year has been smaller, while since 2018, this rate has increased significantly thus making the trend exponential in nature [ 3 ].
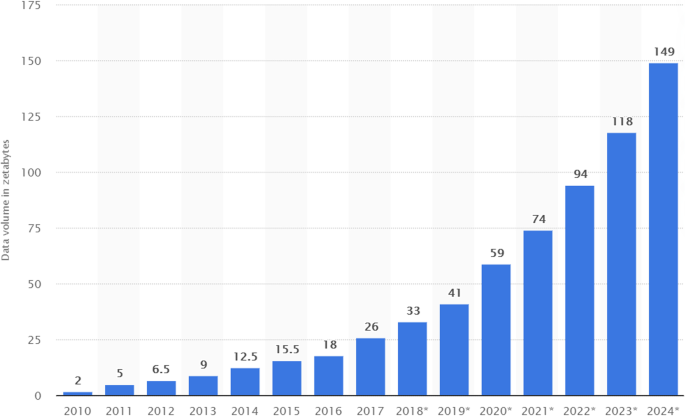
Volume of data/information created, captured, copied, and consumed worldwide from 2010 to 2024 (estimated) [ 3 ]
To get a glimpse of the amount of data that is generated on a daily basis, let’s see a portion of data that different platforms produce. On the Internet, there is so much information at our fingertips. We add to the stockpile everytime we look for answers from our search engines. As a results Google now produces more than 500,000 searches every second (approximately 3.5 billion search per day) [ 5 ]. By the time of writing this article, this number must have changed! Social media on the other hand is a massive data producer.
People’s ‘love affair’ with social media certainly fuels data creation. Every minute, Snapchat users share 527,760 photos, more than 120 professionals join LinkedIn, users watch 4,146,6000 Youtube videos, 456,000 are sent to Twitter and Instagram users post 46,740 photos [ 5 ]. Facebook remains the largest social media platform, with over 300 million photos uploaded every day with more than 510,000 comments posted and 293,000 statuses updated every minute.
With the increase in the number and quantity of data, there have been advantages but also challenges as systems for managing relational databases and other traditional systems have difficulties in processing and analyzing this quantity. For this reason, the term ‘big data’ arose not only to describe the amount of data but also the need for new technologies and ways of processing and analyzing this data. Cloud Computing has facilitated data storage, processing and analysis. Using Cloud we have access to almost limitless storage and computer power offered by different vendors. Cloud delivery models such as: IAAS (Infrastructure as a Service), PAAS (Platform as a Service) can help organisations across different sectors handle Big Data easier and faster. The aim of this paper is to provide an overview of how analytics of Big Data in Cloud Computing can be done. For this we use Google’s platform BigQuery which is a serverless data warehouse with built-in machine learning capabilities. It’s very robust and has plenty of features to help with the analytics of different size and type of data.
What is big data?
Many authors and organizations have tried to provide a definition of ‘Big Data’. According to [ 6 ] “Big Data refers to data volumes in the range of exabytes and beyond”. In Wikipedia [ 7 ] big data is defined as an accumulation of datasets so huge and complex that it becomes hard to process using database management tools or traditional data processing applications, while the challenges include capture, storage, search, sharing, transfer, analysis, and visualization.
Sam Madden from Massachusetts Institute of Technology (MIT) considers” Big Data” to be data that is too big, too fast, or too hard for existing tools to process [ 8 ]. By too big, it means data that is at the petabyte level and that comes from various sources. By ‘too fast’ it means data growth which is fast and should also be processed quickly. By too hard it means the difficulty that arises as a result the data not adapting to the existing processing tools [ 9 ]. In PCMag (one of the most popular journals on technological trends), Big data refers to the massive amounts of data that is collected over time that are difficult to analyze and handle using common database management tools [ 10 ]. There are many other definitions for Big Data, but we consider that these are enough to gain an impression on this concept.
Features and characteristics of big data
One question that researchers have struggled to answer is what might qualify as ‘big data’? For this reason, in 2001 industry analyst Doug Laney from Gartner introduced the 3 V model which are three features that must complement the data to be considered” big data”: volume, velocity, variety . Volume is a property or characteristic that determines the size of data, usually reported in Terabyte or Petabyte. For example, social networks like Facebook store among others photos of users. Due to the large number of users, it is estimated that Facebook stores about 250 billion photos and over 2.5 trillion posts of its users. This is an extremely large amount of data that needs to be stored and processed. Volume is the most representative feature of ‘big data’ [ 8 ]. In terms of volume, tera or peta level data is usually considered ‘big’ although this depends on the capacity of those analyzing this data and the tools available to them [ 8 ]. Figure 2 shows what each of the three V's represent.
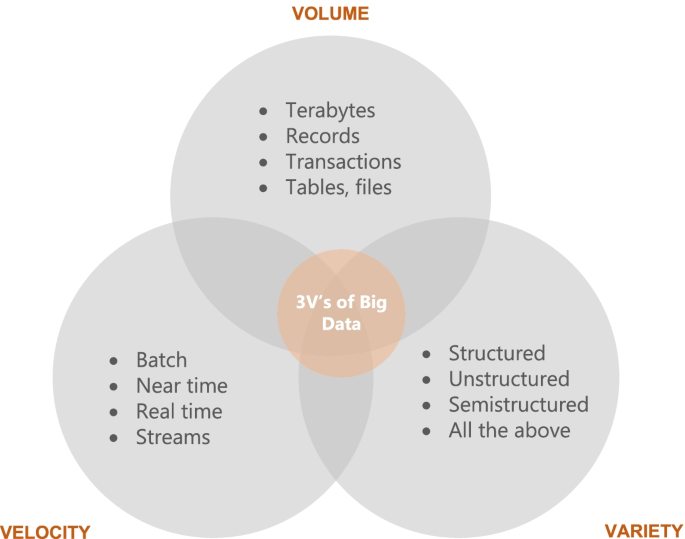
3 V’s of Big Data [ 6 ]
The second property or characteristic is velocity . This refers to the degree to which data is generated or the speed at which this data must be processed and analyzed [ 8 ]. For example, Facebook users upload more than 900 million photos a day, which is approximately 104 uploaded photos per second. In this way, Facebook needs to process, store and retrieve this information to its users in real time. Figure 3 shows some statistics obtained from [ 11 ] which show the speed of data generation from different sources. As can be seen, social media and the Internet of Things (IoT) are the largest data generators, with a growing trend.
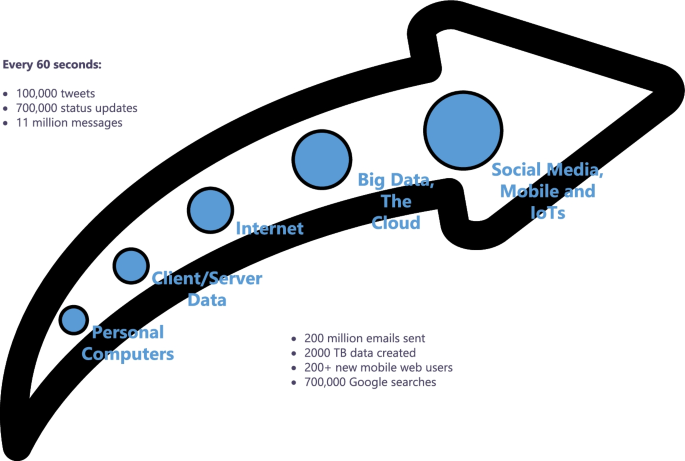
Examples of the velocity of Big Data [ 9 ]
There are two main types of data processing: batch and stream. In batch, processing happens in blocks of data that have been stored over a period of time. Usually data processed in batch are big, so they will take longer to process. Hadoop MapReduce is considered to be the best framework for processing data in batches [ 11 ]. This approach works well in situations where there is no need for real-time analytics and where it is important to process large volumes of data to get more detailed insights.
Stream processing, on the other hand, is a key to the processing and analysis of data in real time. Stream processing allows for data processing as they arrive. This data is immediately fed into analytics tools so the results are generated instantly. There are many scenarios where such an approach can be useful such as fraud detection, where anomalies that signal fraud are detected in real time. Another use case would be online retailers, where real-time processing would enable them to compile large histories of costumer interactions so that additional purchases could be recommended for the costumers in real time [ 11 ].
The third property is variety , which refers to different types of data which are generated from different sources. “Big Data” is usually classified into three major categories: structured data (transactional data, spreadsheets, relational databases etc.), semi-structured (Extensible Markup Language - XML, web server logs etc) and unstructured (social media posts, audio, images, video etc.). In the literature, as a fourth category is also mentioned ‘meta-data’ which represents data about data. This is also shown in Fig. 4 . Most of the data today belong to the category of unstructured data (80%) [ 11 ].
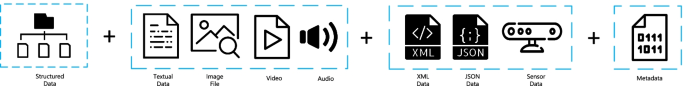
Main categories of data variety in Big Data [ 9 ]
Over time, the tree features of big data have been complemented by two additional ones: veracity and value . Veracity is equivalent to quality, which means data that are clean and accurate and that have something to offer [ 12 ]. The concept is also related to the reliability of data that is extracted (e.g., costumer sentiments in social media are not highly reliable data). Value of the data is related to the social or economic value data can generate. The degree of value data can produce depends also on the knowledge of those that make use of it.
Big data analytics in cloud computing
Cloud Computing is the delivery of computing services such as servers, storage, databases, networking, software, analytics etc., over the Internet (“the cloud”) with the aim of providing flexible resources, faster innovation and economies of scale [ 13 ]. Cloud computing has revolutionized the way computing infrastructure is abstracted and used. Cloud paradigms have been extended to include anything that can be considered as a service (hence x a service). The many benefits of cloud computing such as elasticity, pay-as-you-go or pay-per-use model, low upfront investment etc., have made it a viable and desirable choice for big data storage, management and analytics [ 13 ]. Because big data is now considered vital for many organizations and fields, service providers such as Amazon, Google and Microsoft are offering their own big data systems in a cost-efficient manner. These systems offer scalability for business of all sizes. This had led to the prominence of the term Analytics as a Service (AaaS) as a faster and efficient way to integrate, transform and visualize different types of data. Data Analytics.
Big data analytics cycle
According to [ 14 ] processing big data for analytics differs from processing traditional transactional data. In traditional environments, data is first explored then a model design as well as a database structure is created. Figure 5 . depicts the flow of big data analysis. As can be seen, it starts by gathering data from multiple sources, such as multiple files, systems, sensors and the Web. This data is then stored in the so called” landing zone” which is a medium capable of handling the volume, variety and velocity of data. This is usually a distributed file system. After data is stored, different transformations occur in this data to preserve its efficiency and scalability. Afer that, they are integrated into particular analytical tasks, operational reporting, databases or raw data extracts [ 14 ].
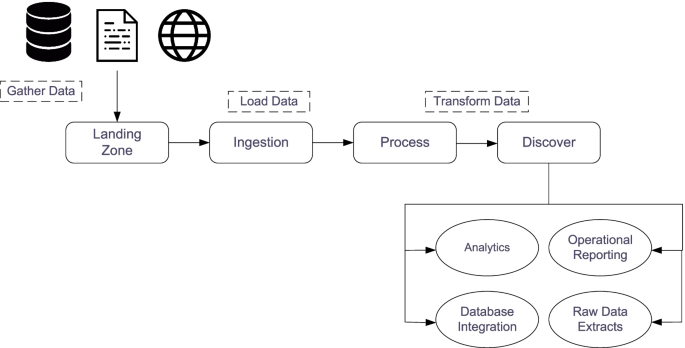
Flow in the processing of Big Data [ 11 ]
Moving from ETL to ELT paradigm
ETL (Extract, Transform, Load) is about taking data from a data source, applying the transformations that might be required and then load it into a data warehouse to run reports and queries against them. The downside of this approach or paradigm is that is characterized by a lot of I/O activity, a lot of string processing, variable transformation and a lot of data parsing [ 15 ].
ELT (Extract, Load, Transform) is about taking the most compute-intensive activity (transformation) and doing it not in an on-premise service which is already under pressure with regular transaction-handling but instead taking it to the cloud [ 15 ]. This means that there is no need for data staging because data warehousing solution is used for different types.
of data including those that are structured, semi-structured, unstructured and raw. This approach employs the concept of” data lakes” that are different from OLAP (Online Analytical Processing) data warehouses because they do not require the transformation of data before loading them [ 15 ]. Figure 6 illustrates the differences between the two paradigms. As seen, the main difference is where transformation process takes place.
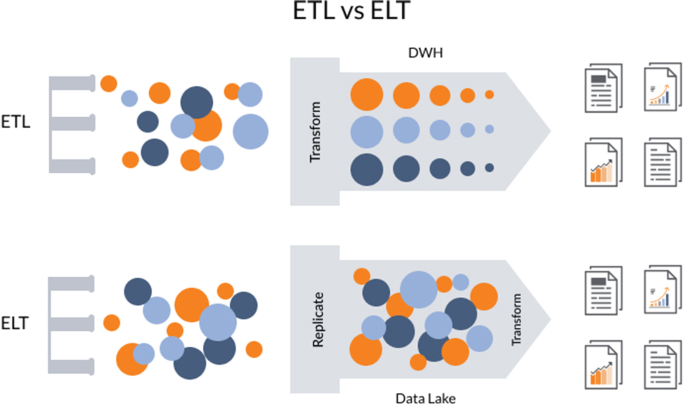
Differences between ETL and ELT [ 15 ]
ELT has many benefits over traditional ETL paradigm. The most crucial, as mentioned, is the fact that data of any format can be ingested as soon as it becomes available. Another one is the fact that only the data required for particular analysis can be transformed. In ETL, the entire pipeline and structure of the data in the OLAP may require modification if the previous structure does not allow for new types of analysis [ 16 ].
Some advantages of big data analytics
As mentioned, companies across various sectors in the industry are leveraging Big Data in order to promote decision making that is data-driven. Besides tech industry, the usage and popularity of Big Data has expanded to include healthcare, governance, retail, supply chain management, education etc. Some of the benefits of Big Data Analytics mentioned in [ 17 ] include:
Data accumulation from different sources including the Internet, online shopping sites, social media, databases, external third-party sources etc.
Identification of crucial points that are hidden within large datasets in order to influence business decisions.
Identification of the issues regarding systems and business processes in real time.
Facilitation of service/product delivery to meet or exceed client expecations.
Responding to customer requests, queries and grievances in real time.
Some other benefits according to [ 16 ] are related to:
Cost optimization - One of the biggest advantages of Big Data tools such as Hadoop or Spark is that they offer cost advantages to businesses regarding the storage, processing and analysis of large amounts of data. Authors mention the logistics industry as an example to highlight the cost-reduction benefits of Big Data. In this industry, the cost of product returns is 1.5 times higher than that of actual shipping costs. With Big Data Analytics, companies can minimize product return costs by predicting the likelihood of product returns. By doing so, they can then estimate which products are most likely to be returned and thus enable the companies to take suitable measures to reduce losses on returns.
Efficiency improvements - Big Data can improve operational efficiency by a margin. Big Data tools can amass large amounts of useful costumer data by interacting and gaining their feedback. This data can then be analyzed and interpreted to extract some meaningful patterns hidden within such as customer taste and preferences, buying behaviors etc. This in turn allows companies to create personalized or tailored products/services.
Innovation - Insights from Big Data can be used to tweak business strategies, develop new products/services, optimize service delivery, improve productivity etc. These can all lead to more innovation.
As seen, Big Data Analytics has been mostly leveraged by businesses, but other sectors have also benefited. For example, in healthcare many states are now utilizing the power of Big Data to predict and also prevent epidemics, cure diseases, cut down costs etc. This data has also been used to establish many efficient treatment models. With Big Data more comprehensive reports were generated and these were then converted into relevant critical insights to provide better care [ 17 ].
In education, Big Data has also been used extensively. They have enabled teachers to measure, monitor and respond in real-time to student’s understanding of the material. Professors have created tailor-made materials for students with different knowledge levels to increase their interest [ 18 ].
Case study: GOOGLE’S big query for data processing and analytics
Google Cloud Platform contains a number of services designed to analyze and process big data. Throughout this paper we have described and discussed the architecture and main components of Biguery as one of the most used big data processing tools in GCP. BigQuery is a fully-managed, serverless data warehouse that enables scalable analysis over petabytes of data. It is a Platform as a Service (PaaS) that supports querying using ANSI SQL. It also has built-in machine learning capabilities. Since its launch in 2011 it has gained a lot of popularity and many big companies have utilized it for their data analytics [ 19 ].
From a user perspective, BigQuery has an intuitive user interface which can be accessed in a number of ways depending on user needs. The simplest way to interact with this tool is to use its graphical web interface as shown in Fig. 7 . Slightly more complicated but faster approaches include using cloud console or Bigquery APIs. From Fig. 7 Bigquery web interface offers you the options to add or select existing datasets, schedule and construct queries or transfer data and display results.

BigQuery Interface
Data processing and query construction occurs under the sql workspace section, Bigquery offers a rich sql-like syntax to compute and process large sets of data, it operates on relational datasets with well-defined structure including tables with specified columns and types. Figure 8 shows a simple query construction syntax and highlights its execution details. Data displayed under query results shows main performance components of the executed query starting from elapsed time, consumed slot time, size of data processed, average and maximum wait, write and compute times. Query defined in Fig. 8 combines three datasets which contain information regarding Covid-19 reported cases, deaths and recoveries from more than 190 countries through year 2020 till January 2021. Google BigQuery is flexible in a way that allows you to use and combine various datasets suitable for your task easily and with small delays. It contains an ever growing list of public datasets at your disposal and also offers the options to create, edit and import your own. Figure 9 shows the process of adding a table to the newly created dataset. From the Fig. 9 , we see that for table creation as a source we have used a local csv file, this file will be used to create table schema and populate it with data, aside from local upload option as a source to create the table we can use Google BigTable, Google Cloud Storage or Google Drive. The newly created table with its respective data then is ready to be used to construct queries and obtain new insights as shown in Fig. 8 .
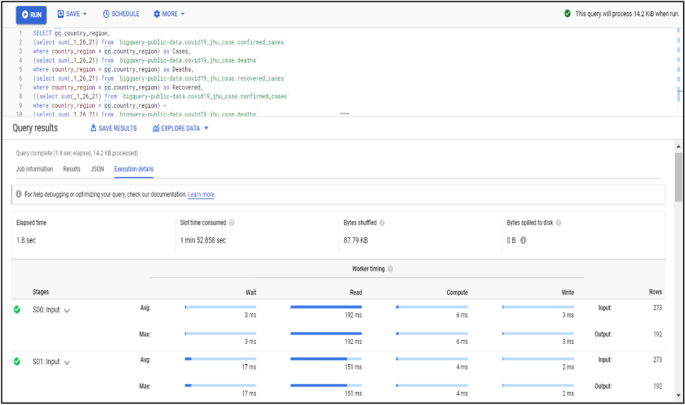
BigQuery execution details
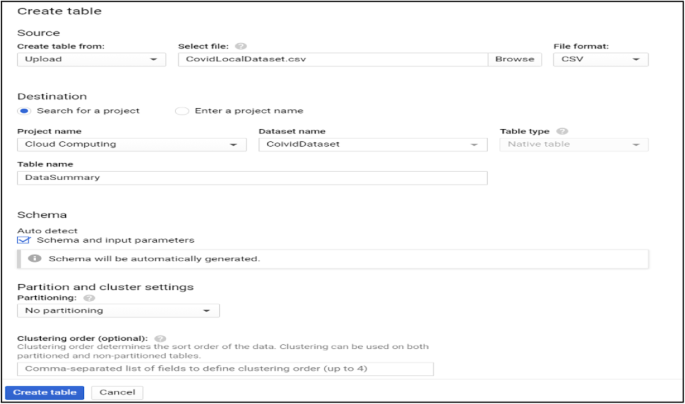
Adding table to the created dataset
One advantage of using imported data in the cloud is the option to manage its access and visibility in the cloud project and cloud members scope. Depending from the way of use, queried data can be saved directly to the local computer through the use of “save results” option from Fig. 8 which offers a variety of formats and data extensions settings to choose from but can also be explored in different configurations using “explore data” option. You can also save constructed queries for later use or schedule query execution interval for more accurate data transmutation through API endpoints. Figure 10 shows how much the average compute time will change/increase with the increase in the size of the dataset used.
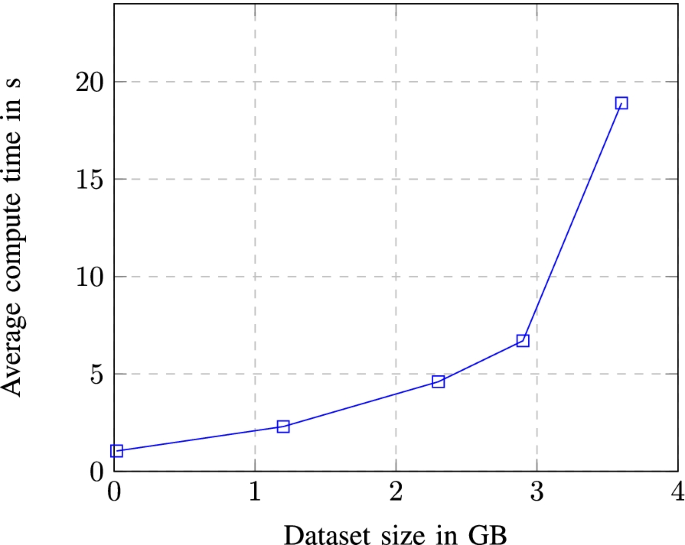
Average compute time dependence in dataset size
Experiments with different dataset sizes
Before moving to data exploration lets analyze performance results of BigQuery in simple queries with variable dataset sizes. In Table 1 we have shown the query execution details of five simple select queries done on five different datasets. The results are displayed against six different performance categories, from the data we see a correlation between size of the dataset and its average read, write and compute.
From the graph we see that the dependence between dataset size and average compute size is exponential, meaning that with the increase in data size, average compute time is exponentially increased.
Data returned from constructed queries aside from being displayed in a simple tabular form or as a JSON object can also be transferred to data studio which is an integrated tool to better display and visualize gathered information. One way of displaying queried data from Fig. 8 with data studio tool is shown in Fig. 11 . In this case a bar table chart visualization option is chosen.
Using data studio for data visualization
Big Data is not a new term but has gained its spotlight due to the huge amounts of data that are produced daily from different sources. From our analysis we saw that big data is increasing in a fast pace, leading to benefits but also challenges. Cloud Computing is considered to be the best solution for storing, processing and analyzing Big Data. Companies like Amazon, Google and Microsoft offer their public services to facilitate the process of dealing with Big Data. From the analysis we saw that there are multiple benefits that Big Data analytics provides for many different fields and sectors such as healthcare, education and business. We also saw that because of the interaction of Big Data with Cloud Computing there is a shift in the way data is processed and analyzed. In traditional settings, ETL is used whereas in Big Data, ELT is used. We saw that the latter has clear advantages when compared to the former.
From our case study we saw that BigQuery is very good for running complex analytical queries, which means there is no point in running queries that are doing simple aggregation or filtering. BigQuery is suitable for heavy queries, those that operate using a big set of data. The bigger the dataset, the more it is likely to gain in performance. This is when compared to the traditional relational databases,as BigQuery implements different parallel schemas to speed up the execution time.
BigQuery doesn’t like joins and merging data into one table gets a better execution time. It is good for scenarios where data does not change often as it has built-in cache. BigQuery can also be used when one wants to reduce the load on the relational database as it offers different options and configurations to improve query performance. Also pay as you go service can be used where charges are made based on usage or flat rate service which offers a specific slot rate and charges in daily, monthly or yearly plan.
Availability of data and materials
The datasets used during the current study are available from the corresponding author on reasonable request. The authors declare that they have no funder.
Hillbert M, Lopez P (2011) The world’s technological capacity to store, communicate and compute information. Science III:62–65
Google Scholar
J. Hellerstein,“ Gigaom Blog,”2019. Available: https://gigaom.com/2008/11/09/mapreduce-leads-the-way-for-parallelprogramming/ . Accessed 20 Jan 2021
Statista,“Statista,“2020. Available: https://www.statista.com/statistics/871513/worldwide-data-created/ . Accessed 21 Jan 2021
Reinsel D, Gantz J, Rydning J (2017) Data age 2025: the evolution of data to-life critical. International Data Corporation, Framingham
Forbes, “Forbes”, 2020. Available: https://www.forbes.com/sites/bernardmarr/2018/05/21/how-muchdata-do-we-create-every-day-the-mind-blowing-stats-everyone-shouldread/?sh=5936b00460ba
Kaisler S, Armour F, Espinosa J (2013) Big data: issues and challenges moving forward, Wailea, Maui, HI, s.n, pp 995–1004
Wikipedia,“ Wikipedia,” 2018. Available: https://www.en.wikipedia.org/wiki/Bigdata/ . Accessed 4 Jan 2021
D. Gewirtz,“ ZDNet,” 2018. Available: https://www.zdnet.com/article/volume-velocity-and-varietyunderstanding-the-three-vs-of-big-data/ . Accessed 1 Jan 2021
Weathington J (2012) Big Data Defined. Tech Republic. https://www.techrepublic.com/article/big-data-defined/
PCMagazine,“ PC Magazine,” 2018. Available: http://www.pcmag.com/encyclopedia/term/62849/big-data . Accessed 9 Jan 2021
Akhtar SMF (2018) Big Data Architect’s Handbook, Packt
WhishWorks, “WhishWorks”, 2019. Available: https://www.whishworks.com/blog/data-analytics/understanding-the3-vs-of-big-data-volume-velocity-and-variety/ . Accessed 23 Jan 2021
Yadav S, Sohal A (2017) Review paper on big data analytics in Cloud computing. Int J Comp Trends Technol (IJCTT) IX. 49(3);156-160
Kimball R, Ross M (2013) The data warehouse toolkit: the definitive guide to dimensional modeling, 3rd edn. John Wiley & Sons
LaprinthX, “LaprinthX,”2018. Available: https://laptrinhx.com/better-faster-smarter-elt-vs-etl-2084402419/ . Accessed 22 Jan 2021
Xplenty, “XPlenty, ”, 2019. Available: https://www.xplenty.com/blog/etl-vs-elt/# . Accessed 20 Jan 2021
Forbes,“Forbes,”,2018. Available: https://www.forbes.com/sites/forbestechcouncil/2019/11/06/fivebenefits-of-big-data-analytics-and-how-companies-can-getstarted/?sh=7e1b901417e4 . Accessed 13 Jan 202
EDHEC, “EDHEC, ”, 2019. Available: https://master.edhec.edu/news/three-ways-educators-are-using-bigdata-analytics-improve-learning-process# . Accessed 6 Jan 2021
Google Cloud, “BigQuery, ”, 2020. Available: https://cloud.google.com/bigquery . Accessed 5 Jan 2021
Download references
Acknowledgements
The authors would like to thank the colleageous and professors from the University of Prishtina for their insightful comments and suggestions that helped in improving the quality of the paper.
The authors declare that they have no funder.
Author information
Authors and affiliations.
Faculty of Electrical and Computer Engineering, Department of Computer Engineering, University of Prishtina, 10000, Prishtina, Kosovo
Blend Berisha, Endrit Mëziu & Isak Shabani
You can also search for this author in PubMed Google Scholar
Contributions
Blend Berisha wrote the Introduction, Features and characteristics of Big Data and Conclusions. Endrit Meziu wrote Big Data¨ Analytics in Cloud Computing and part of the case study. Isak Shabani has contributed in the methodology, resources and in supervising the work process. All authors prepared the figures and also reviewed the manuscript. The author(s) read and approved the final manuscript.
Corresponding author
Correspondence to Isak Shabani .
Ethics declarations
Ethics approval and consent to participate.
Not applicable.
Consent for publication
Competing interests.
The authors declare that they have no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions

About this article
Cite this article.
Berisha, B., Mëziu, E. & Shabani, I. Big data analytics in Cloud computing: an overview. J Cloud Comp 11 , 24 (2022). https://doi.org/10.1186/s13677-022-00301-w
Download citation
Received : 08 April 2022
Accepted : 24 July 2022
Published : 06 August 2022
DOI : https://doi.org/10.1186/s13677-022-00301-w
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cloud computing
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
- Publications
- News and Events
- Education and Outreach
Software Engineering Institute
Sei digital library, latest publications, embracing ai: unlocking scalability and transformation through generative text, imagery, and synthetic audio, august 28, 2024 • webcast, by tyler brooks , shannon gallagher , dominic a. ross.
In this webcast, Tyler Brooks, Shannon Gallagher, and Dominic Ross aim to demystify AI and illustrate its transformative power in achieving scalability, adapting to changing landscapes, and driving digital innovation.
Counter AI: What Is It and What Can You Do About It?
August 27, 2024 • white paper, by nathan m. vanhoudnos , carol j. smith , matt churilla , shing-hon lau , lauren mcilvenny , greg touhill.
This paper describes counter artificial intelligence (AI) and provides recommendations on what can be done about it.
Using Quality Attribute Scenarios for ML Model Test Case Generation
August 27, 2024 • conference paper, by rachel brower-sinning , grace lewis , sebastián echeverría , ipek ozkaya.
This paper presents an approach based on quality attribute (QA) scenarios to elicit and define system- and model-relevant test cases for ML models.
3 API Security Risks (and How to Protect Against Them)
August 27, 2024 • podcast, by mckinley sconiers-hasan.
McKinley Sconiers-Hasan discusses three API risks and how to address them through the lens of zero trust.
Lessons Learned in Coordinated Disclosure for Artificial Intelligence and Machine Learning Systems
August 20, 2024 • white paper, by allen d. householder , vijay s. sarvepalli , jeff havrilla , matt churilla , lena pons , shing-hon lau , nathan m. vanhoudnos , andrew kompanek , lauren mcilvenny.
In this paper, the authors describe lessons learned from coordinating AI and ML vulnerabilities at the SEI's CERT/CC.
On the Design, Development, and Testing of Modern APIs
July 30, 2024 • white paper, by alejandro gomez , alex vesey.
This white paper discusses the design, desired qualities, development, testing, support, and security of modern application programming interfaces (APIs).
Evaluating Large Language Models for Cybersecurity Tasks: Challenges and Best Practices
July 26, 2024 • podcast, by jeff gennari , samuel j. perl.
Jeff Gennari and Sam Perl discuss applications for LLMs in cybersecurity, potential challenges, and recommendations for evaluating LLMs.
Capability-based Planning for Early-Stage Software Development
July 24, 2024 • podcast, by anandi hira , bill nichols.
This SEI podcast introduces capability-based planning (CBP) and its use and application in software acquisition.
A Model Problem for Assurance Research: An Autonomous Humanitarian Mission Scenario
July 23, 2024 • technical note, by gabriel moreno , anton hristozov , john e. robert , mark h. klein.
This report describes a model problem to support research in large-scale assurance.
Safeguarding Against Recent Vulnerabilities Related to Rust
June 28, 2024 • podcast, by david svoboda.
David Svoboda discusses two vulnerabilities related to Rust, their sources, and how to mitigate them.
- Skip to main content
- Skip to search
- Skip to footer
Products and Services

CCNP Enterprise certification
Demonstrate your expertise in enterprise infrastructure, assurance, security, and more. Configure, troubleshoot, and manage the networks of the largest companies in the world with the Cisco Certified Network Professional (CCNP) Enterprise certification.
Empower the world's biggest networks

CCNP Enterprise
Earning a CCNP Enterprise certification demonstrates your ability to scale and maintain enterprise networks to meet growing demands. Showcase your expertise in enterprise infrastructure, virtualization, assurance, security, and automation to influential employers.
Dual stack architecture
Understand Cisco's solutions for managing networks, including configuring the quality of service settings, and switching between hardware and software.
Virtualization
Demonstrate your understanding of virtualization software, virtual machines, and virtual switches. Showcase your ability to divide and manage data paths and create virtual networks.
Infrastructure
Set up and troubleshoot communication protocols. Set up wireless networks and configure features like network time protocol and Network Address Translation/Port Address Translation (NAT/PAT).
Network assurance
Be able to diagnose and fix network problems. Configure and verify various networking features for optimal performance.
How it works
No formal prerequisites.
Learners often have three to five years of experience implementing enterprise network solutions.
Common learner profiles
Professional-level certifications expand on the foundations of associate-level certifications. They cover more advanced topics and allow candidates to hone in on a specific focus area of their choice. Many professional-level certification candidates are looking to prove they’re the best of the best in a specialized field.

Getting started
To earn this certification, you'll need to pass two exams:
- A core exam
- One of seven CCNP Enterprise concentration exams
You'll have access to many resources — from guided learning to self-study and a community forum — that are designed to help you pass your exams.

Unlock your career potential
Your CCNP Enterprise certification proves you can work with complex IT infrastructures - and that opens doors at some of the world’s largest companies.
Potential roles
Network automation engineer.
Use programming and automation tools to streamline network operations.
Systems engineer
Be the expert behind any project that optimizes systems for an organization.
Network support technician
Resolve connectivity issues, troubleshoot devices, and ensure networks are operating smoothly.
Alumni testimonials
Certifications give olivia credibility with employers.

"The knowledge that I’ve got from studying for those certifications gave me the confidence that I’ll always be able to get a job if I need to."
Olivia Wolf, Systems engineer
CCNA, CCNP Enterprise, DevNet Associate
Christoph's certifications earned him a salary boost

"Preparing for certification increased my knowledge and confidence, which ultimately translated to better work performance. As a result, I’ve received generous salary increases."
Christoph Neulinger, Senior network engineer
Getting certified has been a game-changer for AJ

"Cisco Certifications really helped to advance my career."
AJ Murray, Network engineer
Maintain your certification
Your certification is valid for three years. You can renew with Continuing Education credits or retake exams before they expire.
Professional-level Essentials Event: Enterprise
Watch our expert’s guidance and advice on planning your path towards your CCNP Enterprise certification success.
CCNP Enterprise summary
Get a quick primer on the CCNP Enterprise certification and exams.
The CCNP story
Learn why we created the CCNP certifications, and find out how you can use them to plan, support, and grow your career.
Enhance your learning journey
Stay up to date.
Get the latest news about Cisco certifications, plus tools and insights to help you get where you want to go.
Enterprise certifications community
Not sure where to begin? Head to the Cisco Enterprise certifications community to get advice and connect with experts.
- Computer Science and Engineering
Computing: Looking Back and Moving Forward
- Conference: 21st International Conference on Smart Business Technologies
- At: Dijon, France

- Queen Mary, University of London

Discover the world's research
- 25+ million members
- 160+ million publication pages
- 2.3+ billion citations
No full-text available
To read the full-text of this research, you can request a copy directly from the authors.
- Recruit researchers
- Join for free
- Login Email Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google Welcome back! Please log in. Email · Hint Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google No account? Sign up

IMAGES
VIDEO
COMMENTS
A COMPREHENSIVE STUDY ON CLOUD. COMPUTING PARADIGM. Ab Rashid Dar 1, Dr. D. Ravindran 2. 1,2 Department of Computer Science, St. Joseph's College. (Autonomous), Tiruchirappalli Tamil Nadu, (Indi ...
Abstract. Cloud Computing refers to providing computing and communications-related services with the aid of remotely located, network-based resources without a user of such resources having to own ...
Cloud computing has become integral to modern computing infrastructure, offering scalability, flexibility, and cost-effectiveness. Trust is a critical aspect of cloud computing, influencing user decisions in s... Jomina John and John Singh K. Journal of Cloud Computing 2024 13 :134. Research Published on: 21 August 2024.
Cloud Computing is situated to industrialize the IT conveyance of the future. It is a common advancement of the broad selection of numerous specialized progresses in the conveyed computing range ...
This paper presents a meta-analysis of cloud computing research in information systems with the aim of taking stock of literature and their associated research frameworks, research methodology, geographical distribution, level of analysis as well as trends of these studies over the period of 7 years.
Cloud computing has become a widely exploited research area in academia and industry. Cloud computing benefits both cloud services providers (CSPs) and consumers. The security challenges associated with cloud computing have been widely studied in the literature. This systematic literature review (SLR) is aimed to review the existing research studies on cloud computing security, threats, and ...
This research paper presents what cloud computing is, the various cloud models and the overview of the cloud computing architecture, and analyzes the key research challenges present in cloud computing and offers best practices to service providers and enterprises hoping to leverage cloud service to improve their bottom line in this severe economic climate.
The Journal of Cloud Computing, Advances, Systems and Applications (JoCCASA) has been launched to offer a high quality journal geared entirely towards the research that will offer up future generations of Clouds. The journal publishes research that addresses the entire Cloud stack, and as relates Clouds to wider paradigms and topics.
Abstract. We present a meta-analysis of cloud computing research in information systems. The study includes 152 referenced journal articles published between January 2010 to June 2023. We take stock of the literature and the associated research themes, research frameworks, the employed research methodology, and the geographical distribution of ...
Cloud computing stands at the forefront of a technological revolution, fundamentally altering the provisioning, utilization, and administration of computing resources. This paper conducts a comprehensive examination of the visionary aspects, obstacles, and possibilities inherent in cloud computing. It delves deep into the foundational principles and distinguishing features of this technology ...
rent research topics in cloud computing. Finally, the paper concludes in Sect. 7. 2 Overview of cloud computing This section presents a general overview of cloud comput-ing, including its definition and a comparison with related concepts. 2.1 Definitions The main idea behind cloud computing is not a new one.
This systematic study attempts to analyse how the combination of IoT and cloud has been presented and detects the challenges and metrics of such integration. Further, this analysis aims to develop an understanding of the current affair of this integration by overviewing a collection of 38 recent papers.
The cloud literature is analyzed systematically from the management and business point of view. The review is limited with journal articles and papers published between 2014 and 2019. This ...
In this paper, we present a survey of cloud computing, highlighting its key concepts, architectural principles, state-of-the-art implementation as well as research challenges. The aim of this paper is to provide a better understanding of the design challenges of cloud computing and identify important research directions in this increasingly ...
This study aims to synthesise the findings of research on cloud computing adoption and use in libraries. This systematic literature review is based on Preferred Reporting Items for Systematic Revie...
Big Data and Cloud Computing as two mainstream technologies, are at the center of concern in the IT field. Every day a huge amount of data is produced from different sources. This data is so big in size that traditional processing tools are unable to deal with them. Besides being big, this data moves fast and has a lot of variety. Big Data is a concept that deals with storing, processing and ...
Cloud Computing is a network-built handling invention where information is provided to customers on demand. Present Cloud Computing systems holds serious restrictions to protect confidentiality of user's data. Cloud Computing consists of various technologies, policies to ensure data, services and infrastructure protection. The traditional security architecture does not apply because the ...
cellular networking, as well as the open research areas to gain the maximum value from the combination of telecommunication and cloud computing.[2] This paper's comparative results show that the features of each cloud storage system play a significant role in the decision-making process when switching to cloud services.[3] ...
1) Framework: cloud computing systems actually can be considered as a collection of different services, thus the framework of cloud computing is divided into three layers, which are infrastructure layer, platform layer, and application layer (see Fig. 2). Fig. 2: The Framework of Cloud Computing.
Cloud computing can be considered as a new computing archetype that can provide services on demand at a minimal cost. The three well-known and commonly used service models in the cloud paradigm are software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (IaaS). In SaaS, software with the related data is deployed by a cloud service provider, and users can use ...
Gartner (20 19) forecasted that there will b e a 17 percent growth of cloud computing in 2020, which totals to 266.4. billion USD in m arket value from 227.8 billion USD in 2019. Sub sequently ...
The SEI Digital Library provides access to more than 6,000 documents from three decades of research into best practices in software engineering. These documents include technical reports, presentations, webcasts, podcasts and other materials searchable by user-supplied keywords and organized by topic, publication type, publication year, and author.
Student. , M.Sc. I.T., I.C.S. College, Khed, Ratnagri. Abstract: Cloud Computing has come of age later Amazons introduce the first of its kind of cloud services in2006. It is. particularly ...
Earning a CCNP Enterprise certification demonstrates your ability to scale and maintain enterprise networks to meet growing demands. Showcase your expertise in enterprise infrastructure, virtualization, assurance, security, and automation to influential employers.
Big data often lack s structure and comes from. various sources, making it a poor fit for processing w ith a relational database. 2. Related Work. There are many cloud computing and cloud storage ...
Fog computing brings cloud computing storage, networking, and computing capabilities to the edge. The issue of security and safety is one of the most pressing concerns for fog computing systems.