- Day Two DevOps
- Heavy Networking
- Heavy Strategy
- Heavy Wireless
- N Is For Networking
- Network Automation Nerds
- Network Break
- Packet Protector
- Technically Leadership
- Total Network Operations
- The Fat Pipe
- Meet The Hosts
- Networking Tutorials
- Product Demos
- Newsletters
- Open Source Networking Projects
- SD-WAN, SASE, SSE Vendors
- Send Follow Up
- Become A Sponsor
- Pitch Your News
- Join IRC #packetpushers
- Merch Store
Check out our shiny new merch store!


N Is For Networking > Ep. 3 | November 14, 2024
N4n003: what’s a vlan.
Podcast: Download (42.3MB) | Embed

Holly Metlitzky

Ethan Banks
Listen, Subscribe & Follow:
Today we explore Virtual Local Area Networks (VLANs). This topic was prompted by a question from college student Douglas. We’ll explain the fundamental concepts of VLANs, such as their role in segmenting and managing network traffic, and the technical details for implementation. We’ll also address k ey topics including VLAN tags, access and trunk ports, and inter-VLAN communication. Bonus material includes a short discussion of firewalls and VXLAN.
Episode Links:
Heavy Networking
Packet Pushers Community Slack
Episode Transcript:
This episode was transcribed by AI and lightly formatted. We make these transcripts available to help with content accessibility and searchability but we can’t guarantee accuracy. There are likely to be errors and inaccuracies in the transcription.
Automatically Transcribed With Podsqueeze
Ethan Banks 00:00:05 Welcome to N Is For Networking, the short sharp podcast where we explain the jargon, acronyms and concepts of the networking industry in plain language. I’m your co-host, Ethan Banks, a grumpy old network engineer who’s been pushing packets around since the 90s. And with me is co-host Holly Metlitzky, a university grad with a master’s degree working in the networking industry but still somewhat new to the scene. In this episode of N Is For Networking, we are going to discuss another question from my friend Douglas, who sent and he sent in a whole list of questions for us. Douglas did. And Douglas is a college student right now and he asks, what are VLANs and how do they help manage network traffic? What are VLANs and how do they help manage network traffic, Holly, do you have an impression of VLANs, Holly?
Holly Metlitzky 00:00:47 Yeah, I mean, when it comes to VLANs I immediately think of segmenting your network. That’s really where they come up for me in the workplace, mostly for big organizations who are trying to, you know, separate HR from finance, for example, and they are directing or segmenting their broadcast domains into smaller subsets using VLANs. Yeah, that’s kind of my initial, my initial thoughts before diving into it.
Ethan Banks 00:01:17 Segmentation, keyword there and segment the network. And then you said broadcast domains. We’re gonna have to dive into that too. And actually I know we’re going to, I peeked at the show notes. I even wrote some of them. And I know we’re going to talk about, broadcast domains and some, some, in some depth here. So first up, Holly, our VLANs happening at layer two frames or layer three packets?
Holly Metlitzky 00:01:40 Layer two frames for sure.
Ethan Banks 00:01:42 Yeah, exactly.
Holly Metlitzky 00:01:43 Mostly.
Ethan Banks 00:01:44 So so VLAN is virtual LAN, virtual local area network. And in this case we’re talking about Ethernet. It’s an Ethernet virtual LAN. So some, some history here, Holly, that, this would predate you. A local area network. Ethernet would have been a collection of Ethernet hubs, or even not a hub, but a wire, just a physical wire that you would tap into. They had actually, they had a tool called a vampire tap, and you would screw in the vampire tap from your workstation into the backbone wire and make an electrical contact to create an electrical bus and an Ethernet hub, which would be, look much more familiar.
Ethan Banks 00:02:26 You know, it’s a thing with ports on the front. You plug a cable into it. It was the same thing. Basically, architecturally, it’s just a dumb electrical repeater. And that would be a LAN, a local area network. Everybody was plugged into this common wire, this common bus, and saw all the traffic that was going to everyone else. That was a LAN, a local area network, a segment, if you will. Well, virtual LANs come about in the era of switching, and we haven’t talked about the difference between hubs and switches yet on this show. Maybe that’s a, maybe that’s a show for another day too, because we already got too much material for today, Holly. But, virtual LANs allow us to take that concept of a segment and, house multiple segments in one physical switch or spread it across, spread a segment across multiple switches, but still have a contiguous VLAN, even though there can be multiple VLANs there. and that is done with a with a tag, Holly, do you happen to know much about VLAN tags?
Holly Metlitzky 00:03:34 Yeah. I mean, when it comes to VLAN tags, I know you know the range of numbers that you can choose from. you know, 1 to 4094, which I think starts to pose its own issues when you working with huge organizations that are international and so forth. Because even though it seems initially like a big number, which I thought when learning it, they very quickly get used up if you are using a lot of VLANs. .
Ethan Banks 00:04:03 Yeah. So so that VLAN tag exactly what you said. It’s a, it’s a VLAN, that VLAN number is made up of 12 bits. Those 12 bits are part of a larger, tag called .1q tag as in 802.q, the 802.1q being a standard, a standard that was issued by the IEEE. Right, right. I didn’t look that up. Yes, that’s an IEEE standard. Yeah. The guys that, they’re the folks that do all these standards. And and this 32 bit .1q tag contains several different bits of information, but 12 of those bits are for the VLAN tag.
Ethan Banks 00:04:41 And, right, you could have if you did the math knowing, you know, 12 bits, you did the binary and go, wait a minute, that’s 4096 values. So how come we only have VLAN tags one through 4094, zero and the bottom end and 4095 and the top end are reserved for whatever they’re reserved for. And we can only use, we only have those 4094 VLAN tag IDs available to us that we can identify in that .1q tag. But where does that tag live, Holly? Like, could I how would I see it? Where is it?
Holly Metlitzky 00:05:15 Well, I don’t want to get get, start conflating packets and frames, but, I really want to say packet, but I’m not going to say packet, in the frame. It’s a frame header.
Ethan Banks 00:05:28 Yes, it is in, it is, it is part of the Ethernet frame. That is right. That is where that you are going to find that tag. It’s not in the packet. you could find other interesting tags in an IP packet. Things like the table of service byte. You might interpret that as a tag, depending on what you’re using it for. That’s again topic for another day. But right. The .1q tag is part of the Ethernet frame. exactly right. Okay. I got another VLAN question for you, Holly, then. So let’s say we got a switch and we haven’t created any VLANs ourselves. Do you happen to know if there is a default VLAN?
Holly Metlitzky 00:06:07 So there is, it’s usually VLAN 1. As far as I’m aware, I know we, I think it’s across all vendors, it’s VLAN 1. What actually, I’d like to bring up a little bit here, and I know we are short on time. We got to get through this. But you know the difference, between, we don’t call it a default VLAN. We love to call it a native VLAN at Juniper. And I think that’s really because I guess we give our customers the option to change it from 1. From my understanding, that’s kind of the terminology between default and native.
Ethan Banks 00:06:44 So, so in Cisco land, you also have, boy, now, now you got me thinking. I believe you can have a native VLANs as well. Oh, now you got me thinking, Holly. It’s been a while since I set this up, but, yeah, you can have it a native VLAN as well. So but you bring up, let’s back up a second. There are terms that some vendors use around this technology, whether it’s VLANs or really any networking technology. That means the same thing. But we’re using different words. So so so let’s stick with with VLAN tech for a minute here. A concept we haven’t quite talked about yet, but we’re going to get to is the concept of a tagged port or in Cisco parlance, a trunk port. They mean the same thing. It means that that line can carry tagged frames across it. And it’s not a member of a specific VLAN. It’s a member of no VLAN or all VLANs, depending, all depending on how you look at it.
Ethan Banks 00:07:45 Or it’s a it’s a member of all the VLANs you allow to traverse it. Since you can define which VLANs can be allowed across a given port if you want. But again, tag port versus trunk port. All depends on the vendor, but means the same thing.
Holly Metlitzky 00:08:01 Yeah, I had to double check on that because I’m a trunk, trunk port, access port. that’s my my world. So when I’m like, wait, tag, that seems the same thing, but why is there a different word for it? I’m like,
Ethan Banks 00:08:15 And it is, yeah, it is, it is. Yeah. so, so to go back to the default VLAN question. Yeah. Typically default VLAN means you didn’t configure one. There’s nothing there. So every port is going to be a member of VLAN 1. Nothing’s going to have a tag on it. by default it’s you don’t put a tag on a frame unless you are sending it across a shared link that tagged or trunked port, and you need to identify that frame as being part of of a VLAN.
Ethan Banks 00:08:47 So a default VLAN, again, typically VLAN 1. I don’t I can’t think of a vendor that isn’t using VLAN 1 as a default. That is typical. I think there are exceptions because there’s always exceptions and caveats and weird little corner cases in the networking world. And by default, all ports are going to be a member of that default VLAN. So if you take a switch out of the box and don’t configure it at all, you just plug it in, plug or plug hosts into it. Will they be able to communicate? Yes. They’re all going to be part of the default VLAN that all ports on that switch are going to be members of that default VLAN. The thing’s just going to work. even though there’s actually VLANs in there and tagging is possible. And you could have multiple segments in multiple VLANs. So, so Holly, the next thing I wanted to walk us through, what happens when two Ethernet hosts that are connected to the same VLAN and using IPv4 want to talk to each other.
Ethan Banks 00:09:43 And we could say that the sender is, let’s see. It’s 10.0.0.100, the receiver 10.0.0.200. And we’ll just call them .100 for the sender and . 200 for the receiver as we as we go forward. So so what I’m getting at, Holly and I, is IP addresses know each other. But to send that IP packet across the Ethernet wire, what do we have to do with that packet? We got to wrap it in a frame right?
Holly Metlitzky 00:10:08 Yep. Yeah. So now the IP knows of each other but they don’t know about the frames.
Ethan Banks 00:10:16 They don’t know about the frames. They don’t know how to use the physical wire that they’re plugged into or wireless is very similar and what happens here. But they don’t know how to actually, and take this packet and electrically encode it in such a way that it can go on the wire and get delivered to somebody else that’s on that wire. So we’ve got to figure out how do I, who’s the Ethernet recipient that I need to send this thing to, you know your own Ethernet address, but I don’t know, like, Holly, I don’t know your Ethernet address. If we were on the same network, how would we? We might know each other’s like, I know I’m .100 trying to send .200, but the transport I gotta use is this Ethernet thing, so I gotta figure out the frame. So this is the, this is the process that we wanna we want to discuss.
Holly Metlitzky 00:11:04 You’ve gotta ask, someone’s gotta tell you. Someone’s gonna tell you what your Ethernet addresses.
Ethan Banks 00:11:11 And what’s that process of asking?
Holly Metlitzky 00:11:13 So that’s OP or address resolution protocol.
Ethan Banks 00:11:18 And the question is going to show up. If you were to put a packet sniffer on the wire like Wireshark and just have it run and say, show me all the ARP packets, you’ll see ARP Address Resolution protocol, packets. Ha. Frames. Well, it’s a packet too, but yeah, we’re gonna see those on the wire. And so .100, our sender would put an ARP request on the wire broadcasting to all the Ethernet devices, into the VLAN, is anybody out there? .200, hey, I need to send an Ethernet frame to you.
Ethan Banks 00:11:49 Are you .200? If you’re, let me know who you are so I know how to address this Ethernet frame to you. It’s a broadcast. So everybody that’s in that VLAN is going to see that broadcast frame, and .200 is going to reply back to .100 with a, with a unicast as in a directly not broadcast but just send it. I’m not .200. Here’s my MAC address. We talked about MAC addresses in frames versus packets. Our, that was our last episode. Episode 2. So now that .100 knows the MAC address of .200, it can put the destination MAC into the Ethernet frame. It can put the packet into the frame and put the frame on the wire. And now it’s going to get delivered. Does that sound right, Holly?
Holly Metlitzky 00:12:31 Yeah, so it sounds right. I mean, you got to know where you’re sending it to and what the address is, MAC address or just address in general if you don’t want to, you know, stick to networking terminology.
Ethan Banks 00:12:43 Now another little interesting detail is .100 is going to store the information the answer it got back from .200 in its ARP, address resolution protocol cache for future use so that it doesn’t have to put another broadcast ARP on the wire every time it wants to talk to .200, it’s going to cast that answer. And in fact, on most desktops, desktop systems, your Windows computer, your Macs, your Linux boxes, there’s a way to to see your ARP cache. I know on Mac, it’s, you can just do arp-a and it will tell you, here’s all the, the the ARP address resolution protocol entries that I know about. And they have a timeout. They’ll expire eventually because, you know, things change. You can’t have that answer forever. But so why do we go through all that, Holly? And the answer is, goes back to your concept of a broadcast domain. The broadcast is the key part of what we happened here to kind of help us understand VLANs and and segmentation. Every host connected to that Ethernet VLAN saw that broadcast frame. That is our broadcast domain. So let’s say we had a switch with VLAN 1 and a VLAN 2. if I send if I’m in VLAN 1 and I send a broadcast out, does anybody in VLAN 2 see that broadcast?
Holly Metlitzky 00:13:59 No it shouldn’t.
Ethan Banks 00:14:01 No, no it shouldn’t. If it does, you miss cabled something or something’s gone wrong for sure. Yeah. No, it shouldn’t, because that’s what the part of the what the segmentation is all about. You’ve created with a separate VLAN, a separate broadcast domain. So if you’re trying to control what Ethernet device can find each other via broadcast, or you want to limit which hosts can talk to one another, you can create VLANs and put different hosts that you want to separate communications from into different VLANs. And then you can put rules in place saying who can talk to whom across those different VLANs. There’s a little more to the story in that, because I’m kind of implying, Holly, that, if you’re in the same VLAN, you guys can talk no matter what. And, and that’s not actually true.
Holly Metlitzky 00:14:52 That’s not always the case.
Ethan Banks 00:14:53 No it isn’t. There are other things we can do to prevent hosts that are in the same VLAN from talking to each other, but fundamentally, hosts within a VLAN can talk to each other. Although part yeah, part of the world that you’re in, I suppose is about and modern networking is about controlling which host can talk to one another even if they are in the same VLAN. Yeah. Zero trust gets into this concept and well, again, we’ve got to get through this podcast, Holly, there are all these little rabbit trails we can go down. So so here’s a question for you, Holly. See, see what you remember from your studies, how do we make switch ports a member of a VLAN?
Holly Metlitzky 00:15:37 So I guess immediately I’m thinking, okay, what command am I using to assign that switch, like assign the VLAN to the switchboard. But, you know, you got to first define is that port what we discussed earlier access or trunk. So if we want multiple VLANs on that port we’ve got to assign it as a trunk port and then assign those VLANs to that port.
Ethan Banks 00:16:01 And if we just want a switch port to be a member of a single VLAN, that would be an access port. And access as in I have a workstation that needs to access the network. It’s an access port. I’m going to plug it in. And that switchboard is a member of that VLAN. Now, the big difference between an access port and a what you call a trunk port, other network vendors are calling it a tagged port is whether or not you actually have that .1q tag with the VLAN 12 bit identifier inside of it or not. On an access port, no, there’s no reason to have the tag there. If that frame needs to traverse a trunk por,. when it does traverse the trunk port, the switch is going to put the tag on there. That .1q tag will be, it’ll be on there. It’ll be a tagged port therefore a trunk port again, just depending on the vendor.
Ethan Banks 00:16:57 Another question. Well, actually, let me back up a step here. How do VLANs in separate, how do packets, I’m sorry, or frames in separate VLANs talk to each other? Have you run into this, Holly? Actually, I know you’ve run into this. Yeah.
Holly Metlitzky 00:17:12 Yeah, I have, and I was actually working on it the other day, and it’s quite funny because it’s almost you just do it like I knew what I was doing, and then I had to take a step back to think about it, to explain it to somebody else. I’m like, well, they don’t. I’m like like they don’t. If they’re in different VLANs, they shouldn’t speak to each other. So you’ve got to do something to allow them to communicate. And that’s where your routers come in. Now, you know, we can dive into that a little bit, but it’s, they shouldn’t speak to each other. So you’ve got to do something to allow them to communicate.
Ethan Banks 00:17:47 And for today, that’s as far as we need to go. You need a router. You need a router in the middle that’s going to, going to take care of that. It would be because you’re right. VLAN 1, and VLAN 2, separate broadcast domains. They’ve got no path to one another. So how do you get traffic between these VLANs to speak? You use a router. Now that could be and most modern layer you’d call it a layer three switch is they basically modern switches are also routers. They have the ability to do this. So if VLAN 1 needs to talk to VLAN 2, some host in VLAN 1 needs to talk to a host in VLAN 2 the frame is going to be recognized by the switch. The switch will have a, the default gateway for that VLAN on it. And it will have the ability to go okay, so this packet in VLAN 1 needs to talk to a host in VLAN 2 I will route it, I will take the frame decapsulate that frame to the packet, route the packet into the VLAN that needs to go to make it a frame again, re-encapsulate it as a frame and deliver it to the host on the other side. That can all happen in a switch. It can happen among separate switches. And that’s another thing to consider, is that you can have all this functionality again in a single device, or spread out across a ton of devices, you know, dozens, hundreds of switches, potentially. You don’t, you don’t want a huge, huge network like that without having a bunch of layer three separation. In fact, how to scale a network is, again, yet another conversation, Holly. But, you but you could have, here’s a switch that’s got VLAN 1 and the the default gateway for VLAN 1 could be in a different switch down the line somewhere. have that switch down the line, do the routing into VLAN 2 and the host and VLAN 2 is three switches away. And all the switches in between are interconnected along VLAN 2. It could work. It could work like that. All right. So now, now Holly, let’s let’s bring this thing home here with just a couple of closing questions.
Ethan Banks 00:20:04 Is it possible to control which host can talk to each other within a VLAN? Because by default, no. But we do have a few tools. I don’t know if you’ve used any of these.
Holly Metlitzky 00:20:16 I haven’t configured them myself, but I have dealt with usually customers who have this configured already, and now we trying to implement that in a different way. So, you know, certain access lists is usually how we, what I’ve run into.
Ethan Banks 00:20:34 Yep. And there’s a variety of different access list tools and different switching vendors and different switch platforms will have different access list capabilities. Very simple switches may not give you much of any sort of access list. But any, any name brand switch, if you will, Juniper or Cisco, Arista, you’re going to have some kind of access list functionality. And then there are different styles of access lists. And it can get confusing actually looking at a switch configuration, because you might have, for example, a port access list that is an access list literally on a port, on the switch port governing traffic that is coming typically in the direction of in to, not out of, but in to the switch port. So traffic coming from a host into the port, there’s an access list that is filtering that traffic. You also can have VLAN access list depending on the switch, which can govern traffic, in between hosts in the VLAN, and maybe hosts going out of the VLAN depending on the switch, depending on the vendor, depending on how it was implemented. There’s yet another tool, and this is a crazy one, Holly, private VLANs. So you want to have some fun? Get your mind blown a little bit? Go look at private VLANs.
Holly Metlitzky 00:21:45 Yeah. I actually haven’t heard. So that’s a new one to me.
Ethan Banks 00:21:47 I don’t know if they live much these days. I mean, back in the day I had some use cases for private VLANs, and you can make ports. You can make different hosts in the VLAN be able to talk to each other or be completely isolated. And you define the character of each port that’s in the private VLAN a specific way. Like you’re, you’re a host in my private VLAN, I forget all the name nomenclature, but you’re a host basically, and you can’t talk to any other hosts. You can only talk to the router port and you can have a port that’s basically everybody can talk to this port because it’s the port with the router on it. So I don’t want, the use case is, I don’t want anybody on my private island to be able to talk to anybody else on this private VLAN, because they shouldn’t be able to see each other. So a use case for that would be I’ve got a bunch of clients of mine that all need to connect to my network, and they connect to my network, but I don’t need them to connect to each other. I only need them to connect to me. So I LAN them on a private VLAN and make sure the private VLAN is configured so that they can’t talk to each other, but only to the router port that connects them to whatever the assets are that I’m giving them access to. So private, private VLANs. I almost never saw those implemented. I only had ever one use case for it in all my years of doing networking stuff, and then port access list and VLAN access list, I will say it’s not a solution I love if you’re going to do them manually, because it just gets so hard to, to, to maintain these kind of things and track them. But if I’m using a higher level security system that happens to implement the security by using port access lists and I don’t care, at that point it’s up to the security platform to take care of that for me. Great. Works great. Now, so same question, Holly, but just a little different. So that was you know, if by default hosts can talk to each other within a VLAN, but maybe we don’t want them to. What are some tools now what what are our tools if we want to control which host can talk to each other in separate VLANs, and this is much more common I think.
Holly Metlitzky 00:23:54 Yeah. I mean, I guess that’s access lists, not, VLAN, I mean, could be VLAN access list all,but in inter VLAN access list, not intra VLAN access list. Yeah. Or firewalls, you know, if you’re using a security router to do that, routing between your VLANs.
Ethan Banks 00:24:17 Yeah, exactly. So access list, very common use case here where you’d apply them rather than at a switching level, like a port access list or a private VLAN or VLAN access list. You’re just using a, a more, I would say a traditional access list. And you’re applying that at the routing level where you’re filtering packets, because when you’re doing inter VLAN filtering, you’re thinking about, IP packets. And remember from our last conversation, it’s not like a frame can only have an IP packet in it. That just happens to be what we see in modern networking. You could put a whole different, a whole bunch of different things in there. But for our purposes, yeah. you’re talking about an IP access list could filter who’s talking to whom in separate VLANs. I would use those in isolated cases. you know, on a router, specific use cases where it’s like, yeah, that’s the best fit. I would prefer to use firewalls for, for most of that kind of thing. So like in Juniper land that would be an SRX.
Ethan Banks 00:25:13 Yeah. That’s, and you know, I’d rather have that firewall, which is a special device that’s very good at managing, maintaining those things usually has special capabilities, special UIs, maybe, that help with governing those access lists, do do that work. But you don’t always have a firewall in between VLANs, right? Often we do, but not always. So but yeah, there’s, lots of ways to control traffic going in between VLANs. And again, in modern networking, it’s increasingly common to have some sort of controls in place. And the different vendors implement their security solutions in different ways. All right. Last question, Holly. And this I think you might know this one because I know this is one of the areas you, you work in, in your work for Juniper in a VXLAN fabric, VLANs fit into the scheme somehow. What, do you know what goes on there?
Holly Metlitzky 00:26:11 Yeah. So I mean, going back to what I commented on earlier about the number or the limitations of the VLAN quantity, when it gets to VXLAN, you’re going to very quickly run out of VLANs. So they then get mapped to VNIs. So virtual network identifiers to transport them across the fabric. So it really is a numbers game. You’re taking away your VLAN tag. And now replacing with a VNI tag. Do you need to do that? Well you’re going to run out of VLANs very quickly. So you need that VNI.
Ethan Banks 00:26:48 Yeah. If you’re, if you’re a bigger shop for sure. Yeah. The VNI, how many VNIs are there? 16, 16 million. Right. Is that the max number I forget? Yeah.
Holly Metlitzky 00:26:56 Something around there.
Ethan Banks 00:26:58 So. Right. So VXLAN as a, as a fabric, right with the virtual network identifiers, it replaces that concept of a VLAN, if you will, with, with VNIs and and, exactly right. We go from having just over 4000 VLANs to 16 million virtual network identifiers. And when you hand off an Ethernet frame into the VXLAN fabric, you will you are actually encapsulating that entire Ethernet frame in the VXLAN packet. And that VXLAN packet is going to have that VNI assigned. And it’s the common way to deal with this, to map the VLAN that’s coming from into VNI for transport across the VXLAN fabric. It’ll get decapsulated on the other end, and a VLAN identifier will be put back on to the frame if necessary. If we need a, if we need it to be tagged, or just have it put into the correct port. And you don’t have to have contiguous VLANs on either end as I understand it, you can get kind of crazy with your mappings, and there’s use cases where you might want it to be mismatched. You’re nodding your head Holly.
Holly Metlitzky 00:28:05 Yeah. It gets, it gets quite complex very quickly. Yeah. It took me quite a while to wrap my head around this, you know, starting from VLANs. And now suddenly I’m like, oh, I don’t need that and I’ve got 16 million of these VNIs. I’m like, okay, let’s back up.
Ethan Banks 00:28:20 So quick review for all of this. VLANs are segments. Broadcast domains would be the way to think about them. We’re controlling who can see whom by limiting the the broadcast domain scope. VLANs are happening at layer two. And if we’re moving in a switch with multiple VLANs you’re going to have a tag involved an 802.1q tag that includes a 12 bit value. That is that VLAN tag number. Now we talked about a lot of other stuff we talked about, you know, filtering. We talked about mapping to a VXLAN fabric at the end. Some of that was bonus material. You know, if you have any takeaway from this, dear listener, it’s, it’s just to keep in mind that virtual LAN is about that segment and, and keeping network traffic segmented one from another. It’s a security boundary in some regard and or you could use it for performance and for scaling as well. That’s less of a concern than it used to be. But, it used to be we were very concerned about how many hosts were in a broadcast domain, because you get too much broadcast out traffic out there and it slows everybody down. That’s less of a concern these days. But that was a that was a big thing way back in the day that we used to design around. So all right, Holly, how can people follow you on the internet?
Holly Metlitzky 00:29:39 You can find me on LinkedIn. Just search my name, Holly Metlitzky.
Ethan Banks 00:29:43 Excellent. I am Ethan Banks. You can find me on LinkedIn. My other podcasts are Heavy Networking and Tech Bytes, which you can find on the Packet Pushers podcast network at packetpushers.net. And there’s also the Packet Pushers community Slack. Holly and I hang around in the Packet Pushers community Slack and there is an N Is For Networking pod channel. If you’d like to ask us some questions or request topics for us to cover in a future episode, we’d love to hear from you. And thank you for listening to N Is For Networking today. So subscribe if you would tell your friends and hey, this is a new podcast, would you leave a rating on Apple Podcast that’s going to help other people discover the show? Many of you that have heard about the show are really excited about it, said you were telling your friends, really looking forward to it and so on. So leave that rating and it’s going to help other people you don’t even know discover the show. You will find N Is For Networking anywhere that you get your podcasts. Another way you can tell us about topics you want us to cover, packetpushers.net/follow up and we will add whatever your request is to the list. I’ve been doing that all week long. Just remember, networking isn’t hard, other people figured it out, so you can too.
Share this episode
Explore our podcasts, have feedback for the hosts.
We want your follow-up .
A Free Newsletter That Doesn't Suck
Human Infrastructure covers IT blogs, news and vendor announcements of interest to hands-on engineers.

How to Set Up a VLAN in 12 Steps: Creation & Configuration
Shelby Hiter
eSecurity Planet content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More .
Key Takeaways
- Setting up a VLAN is a 12-step process. The steps include preparing unique VLAN IDs, creating a network diagram, configuring switch ports, and assigning switch ports to VLANs. ( Jump to Section )
- Static and dynamic VLANs serve different purposes. They are compared based on advantages based on network size, complexity, and requirements. ( Jump to Section )
- It’s imperative to get the VLAN setup process right and periodically reassess VLAN performance to ensure network security and efficiency. ( Jump to Section )
Setting up a virtual local area network (VLAN) can be a complicated process, especially if you’re operating a large enterprise network, a network with legacy or hybrid architectures, or a network with specific workloads that require additional security and regulatory compliance safeguards.
Each VLAN configuration process will look a little different, depending on the specifications you bring to the table, and some of these steps — particularly steps five through eight — may be completed simultaneously, in a slightly different order, or even in a more automated fashion if you choose to set up a dynamic VLAN.
Still, in general, your network stands the best chance of success if you complete the following 12 VLAN configuration steps and document your processes, strategies, and requirements along the way.
Table of Contents
1. Brainstorm VLAN Groupings
In a traditional local area network with no virtualized barriers, all devices and network components communicate and share information with each other; you’re likely setting up a VLAN in the first place because this foundational setup is too loose for your requirements. But what are the ideal segments that will make your network function optimally and securely?
At this point in VLAN creation and configuration, it’s time to determine what VLAN groupings make the most sense for your network’s strategic complexities. Consider not only how many VLANs you’ll need but also the purpose each VLAN will serve and how they need to be set up to fulfill that purpose. While many organizations stick to more traditional boundaries like physical locations or departments, there may be more effective and secure ways for you to group and set up VLAN rules.
For example, if your company works closely with a third-party professional services firm that needs access to certain HR and security applications and data but not others, you could divide your VLANs based on which ones need looser versus stricter identity and access management controls. From there, determine which users and devices will align with and be assigned to each grouping.
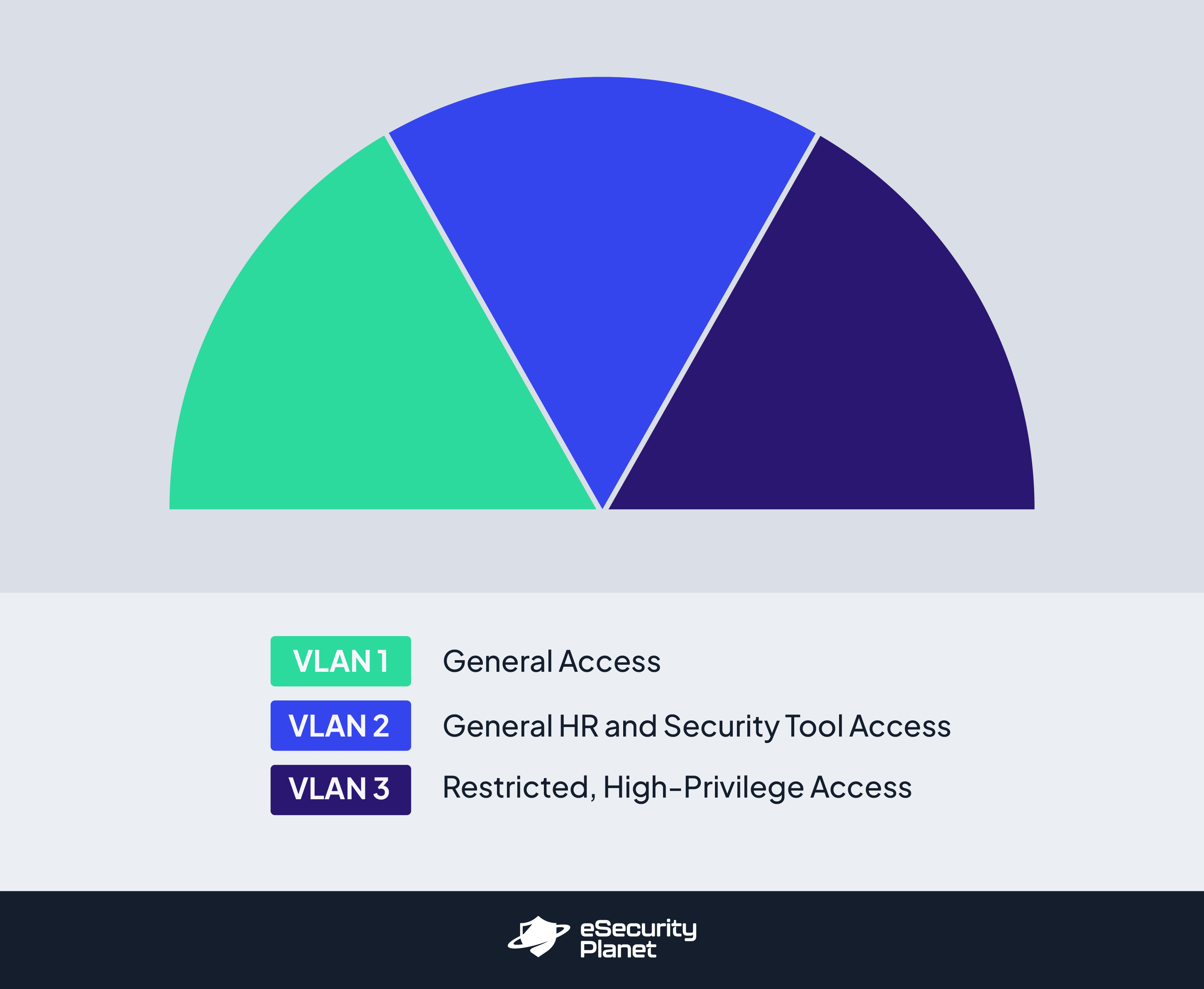
2. Prepare Unique VLAN IDs
Every single VLAN you set up will need a unique VLAN identification number so you can segment network traffic to the appropriate places and keep documentation organized for multiple VLANs simultaneously. VLAN IDs are purely numeric and range from one to 4,095. While you don’t necessarily “need” these VLAN IDs to be operational yet, it’s a good idea to figure them out now so you can use them when labeling your network diagram in the next step.
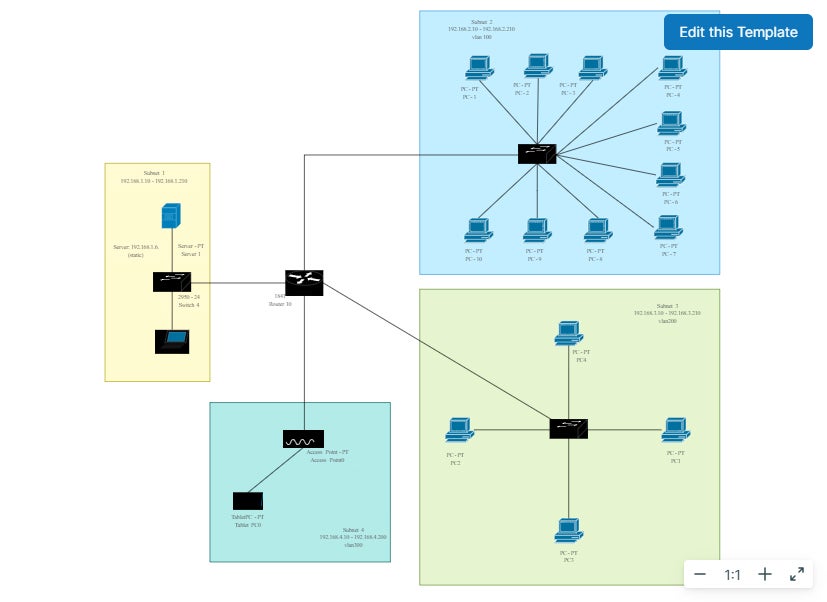
3. Create a Logical Network Diagram or Map
Before you even begin setting up your VLANs and connecting devices and switches, the best way to ensure a successful VLAN network setup is to map out the specificities and relationships of your network with a network diagram. The labels and connections you illustrate at this stage of VLAN creation will give you the labels and organizational structure you need to keep track of all the devices, switches, routers, and other components necessary to fulfill your architectural plans.
Your team may choose to create this diagram manually or with tools that are already in your portfolio. However, a number of free and low-cost network diagramming tools specifically offer templates and icons that make it easier to illustrate the network you’re setting up, often with low-code/no-code interfaces and tools. If you’re interested in finding a network diagramming tool to make this step more efficient, consider investing in one of these top network diagram software and tooling solutions .
4. Optional: Purchase Additional Equipment
Based on the VLAN grouping requirements and design(s) you’ve developed in the previous three steps, you should have a clearer picture of any missing hardware or software that you need to purchase. Perhaps you have more VLAN groupings than you expected and need to bring in additional switches and routers. Or maybe your organization is growing quickly, and you want to purchase new switches with more ports for more devices. There’s also the possibility that you are moving from a primarily on-premises network setup to a hybrid or cloud setup that requires new software or third-party relationships.
Regardless of your new requirements, start by creating an inventory list of any networking equipment you currently own, including information about switch and router formats, configurations, port counts, speeds, and other details pertinent to VLAN setup. From there, make a separate list of the networking tools you’re missing, the cost of these missing tools, and any other specialized information that should be considered during the buying process.
5. Connect Network Devices to Appropriate Switch Ports
You should now connect VLAN servers, end-user devices, and other relevant network devices — as long as their IP addresses are already configured — to the switch ports that have been selected for the corresponding VLAN group. While individual devices, ports, switches, and routers have not yet necessarily been configured in their settings to align with a certain VLAN and function, you should still know which devices and network components have been set aside for which VLANs. If you’re unsure about the switch ports that should be connecting to each device, reference your network diagram (or go back to the network diagramming stage and create a more detailed diagram).
If you are opting to create a dynamic VLAN instead of a static VLAN, steps five through eight may look a little different for you. For example, you may spend these steps creating or identifying the appropriate rule-based protocols for your devices and setting up automation rules rather than manually connecting ports and devices to VLANs.
6. Configure Switch Ports
Now that your devices are connected to the correct switch ports, it’s time to configure the switch ports so they can perform according to their assigned functions. Many of your ports will simply need to be set up as access ports in the switch’s settings; an access port is a simple connection that allows devices to connect to only one VLAN. Access ports are most appropriate for devices and users that will not be using VLAN tagging or participating in inter-VLAN routing.
Trunk ports are also configured in a switch’s settings, but they are designed to manage higher bandwidth traffic and can manage traffic for more than one VLAN. Devices should only be connected to trunk ports if they have been authorized and configured for VLAN tagging and inter-VLAN routing. Before moving on to the next step, double-check that devices are connected to the correct type of switch port for their operational needs.
7. Set up VLAN Specifications via Network Switch Settings
All of the prework is done: It’s time to actually create the virtual local area networks you want through network switch settings. You’ll do this by accessing your network switch management interfaces and going to the section where you can create VLANs. Create the number of VLANs you determined were necessary in previous steps and assign them the unique VLAN IDs you selected in step two.
8. Assign Switch Ports to VLANs
Again, keep in mind that steps five through eight may go in a slightly different order, depending on your team and their preferences. So if you have not yet assigned switch ports to the appropriate VLAN, it’s time to do that now. Tagged ports (trunk ports) are likely already associated with the correct VLANs, but you should confirm that they are set up correctly at this time. For untagged ports (access ports), you’ll need to manually connect them to the correct VLAN. Remember, trunk ports can be associated with more than one VLAN, if appropriate.
9. Optional: Add VLAN Tags
VLAN tagging is the process through which VLAN network traffic is further segmented and specialized. When VLAN tags are in use, associated devices and ports automatically interact with devices and ports that share those same tags; however, tags also give network administrators the power to further direct traffic and support case-by-case inter-VLAN routing scenarios.
VLAN tagging is most appropriate for networks with complex traffic patterns and a diverse range of users, devices, and security permissions. If you choose to set up trunk ports with multiple VLANs running through them, as demonstrated in step six, you’ll need to make sure at least some of your VLANs receive tags so traffic doesn’t get muddled in trunk ports.
If you’re not sure if your network would benefit from VLAN tags, read this in-depth article on the topic to help you make your decision: Tagged vs. Untagged VLAN: When You Should Use Each .

10. Optional: Configure Inter-VLAN Routing
If your network requires VLAN-to-VLAN communication as a part of its regular operations, you’ll want to use the VLAN tags you set up in the previous step to direct inter-VLAN routing. While it sounds counterintuitive to open traffic flow between VLANs, many organizations choose to do this because the different layer at which routers operate makes it possible for them to still control what types of traffic flow across VLANs and when and how devices and users move from VLAN to VLAN. As part of the inter-VLAN configuration step, you may also need to set up or double-check your VLAN access controls, ensuring only approved users and devices can take advantage of inter-VLAN routing.
11. Quality-Test Your VLAN
Now that everything’s set up, it’s time to test network connectivity and performance. Make sure that all devices within the same VLAN are able to interact with each other and, conversely, that they are not able to reach devices in other VLANs. Ping and traceroute are both effective tools for testing VLAN connectivity and performance, but a number of other network security and management tools may be appropriate as well.
12. Document and Reassess VLAN Performance Periodically
Enterprise networks in particular frequently change as more devices and users, new hardware and software requirements, and new operational and security use cases arise. Network administrators and/or network security team members should maintain an up-to-date network diagram, equipment inventory, changelogs, and other configuration documentation so it’s easy to see what the network looks like now, if and where any vulnerabilities have reared their heads, and if any other changes are necessary to improve network performance. Each time you go through this process, update your documentation so you have a full history of the network and what you’ve done to maintain it.
Should You Use a Static VLAN or Dynamic VLAN?
Static and dynamic VLANs bring different advantages to network administrators, depending on the size, complexity, and requirements of their network. Below, we’ve explained how each type works and when you should use it.
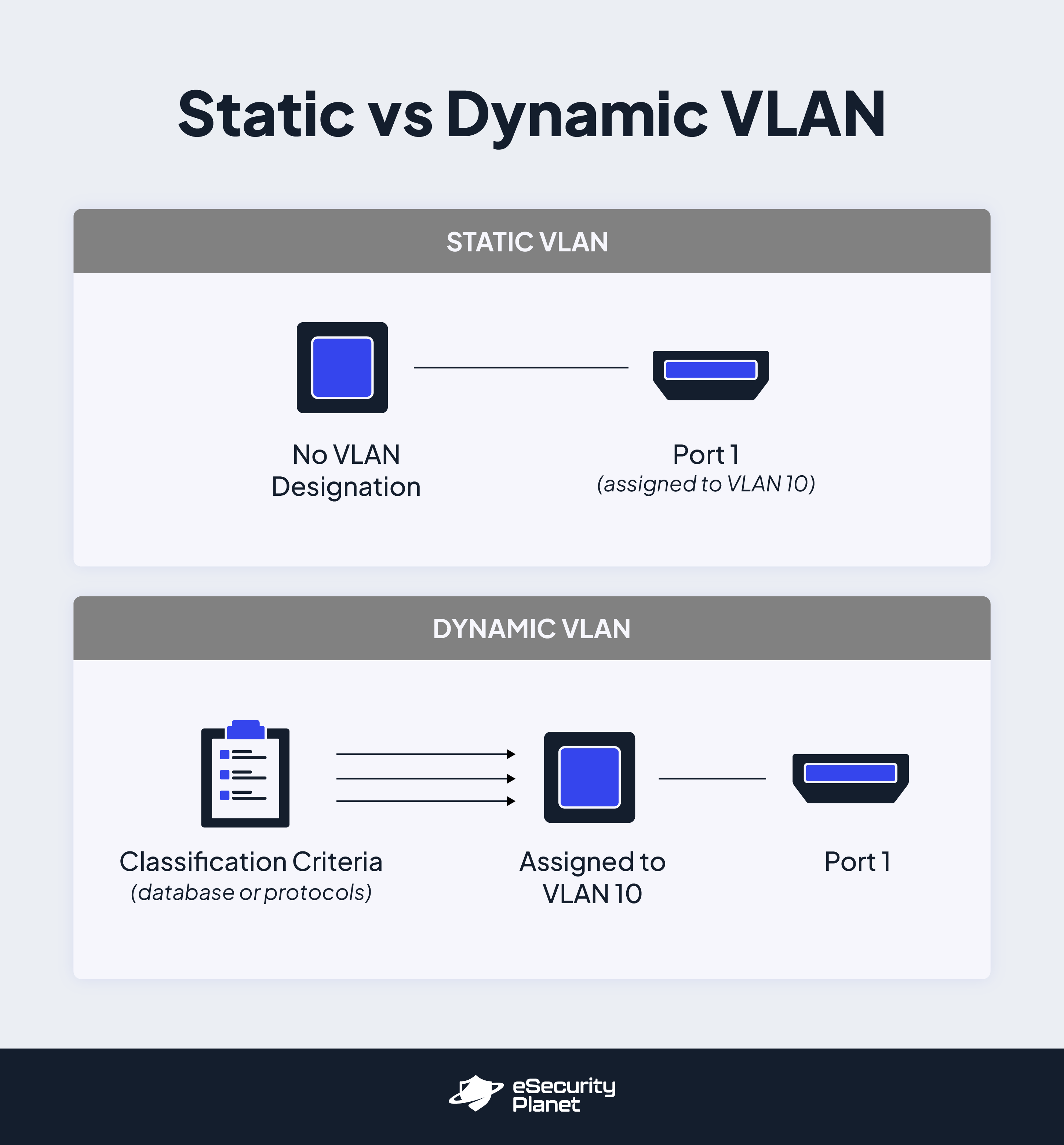
Static VLAN
Static VLANs exist when network administrators manually connect network devices to physical switch ports and those devices receive their VLAN assignment based on that connection. If the device ever needs to be reassigned to a new VLAN, the network administrator would physically connect it to a new switch port that is already associated with that VLAN. In other words, a static VLAN is one in which switch ports are assigned to VLANs and devices are not assigned to VLANs; they receive their orders directly from the switch port they’re connected to.
This type of VLAN is best for smaller networks, or networks that change infrequently and include fewer VLAN segments because network administrators have to manually connect (and sometimes reconnect) devices to the right ports for them to work. With a larger network that’s changing frequently, this task alone could become a full-time job and riddled with errors. Static VLANs are most advantageous for network administrators who need an easy-to-setup VLAN with predictable infrastructure and limited authentication needs.
Dynamic VLAN
A dynamic VLAN is one in which devices are assigned to that VLAN on a dynamic and semi-automated basis. Specialized criteria determine which devices are assigned to which VLANs and when. These criteria may include specialized network access controls and protocols, VLAN membership policy servers (VMPS) and databases, or some other combination of servers and data-driven rules. With a dynamic VLAN, devices are assigned to VLANs while ports frequently are not assigned to particular VLANs; they are simply the conduit through which pre-assigned device traffic flows.
Dynamic VLANs are best for larger and more complex networks that need to maintain frequently changing authentication and usage rules. It’s a much more difficult implementation process when compared to static VLAN, but for more strenuous network rules and requirements, dynamic VLAN ultimately saves network professionals time in the long run, as they can simply update protocols and VMPS entries when new VLAN assignments are needed across multiple devices.
Bottom Line: The Importance of Preparation for Optimal VLAN Performance
While the actual process of setting up a VLAN can be as simple as updating network switch settings and connecting devices to VLAN switch ports, the strategy behind a successful VLAN setup can be much more daunting. You’ll need to consider any specialized security or compliance requirements, the different device types that need access, and the resources and monitoring it will take to set up and sustain an efficient VLAN.
All the steps listed above are crucial aspects of creating and configuring a sustainable VLAN network. But perhaps the most important step of all is documenting your thought process and your network architecture, especially as they change over time. Maintaining detailed documentation will help your existing network and security team members stay on top of the most pertinent network updates and issues while simultaneously ensuring that any future members of the team receive the foundational training necessary to successfully work in your VLAN ecosystem.
Read next: What Is Network Security? Definition, Threats & Protections
Previous article
Next article

Subscribe to Cybersecurity Insider
Strengthen your organization’s IT security defenses by keeping abreast of the latest cybersecurity news, solutions, and best practices.
This field is required
By registering, you agree to the Terms of Use and acknowledge the data practices outlined in the Privacy Policy. You may unsubscribe from these newsletters at any time.

Get your free download!
Enhance your network security with cutting-edge strategies to protect against sophisticated cyber threats. This whitepaper explores next-generation firewall solutions that help you secure, converge, and scale your defenses in a hybrid, multi-cloud world.
By submitting this form, I agree that TechnologyAdvice and vendors sponsoring this content may send me information as outlined in the Terms of Use and Privacy Policy .
Thanks, we’ve received your request
IT Security Resources
Norton vs mcafee: compare antivirus software 2025.

Video: 2.9 Billion Records Compromised in NPD Breach – Recap

Video: Top Cybersecurity Threats That You Need to Fix

Video: How Hackers Steal Your Cookies & How to Stop Them

Top Cybersecurity Companies
Related articles.

5 Best Cybersecurity Certifications to Get in 2025

7 Best Attack Surface Management Software for 2025
What Is a DMZ Network? Definition, Architecture & Benefits

IMAGES
VIDEO